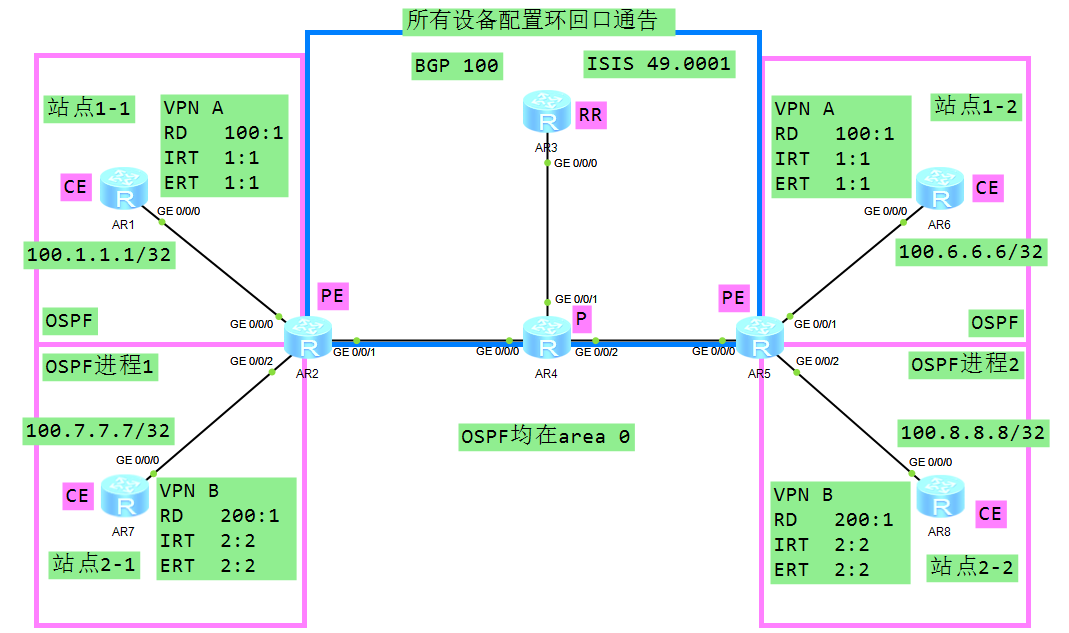
MPLS VPN基本组网:
Intranet组网:一个VPN中的所有用户之间能够进行流量转发,VPN中的用户不能与任何本VPN以外的用户通信,Intranet组网中站点通常是属于同一个组织
Extranet组网:一个VPN中的用户可将部分站点中的网络资源给其他VPN用户进行访问::: tip
Intranet和Extranet组网通过设置RT值实现同一个VPN站点内和不同VPN站点间的数据访问
:::
Intranet场景的MPLS VPN举例:
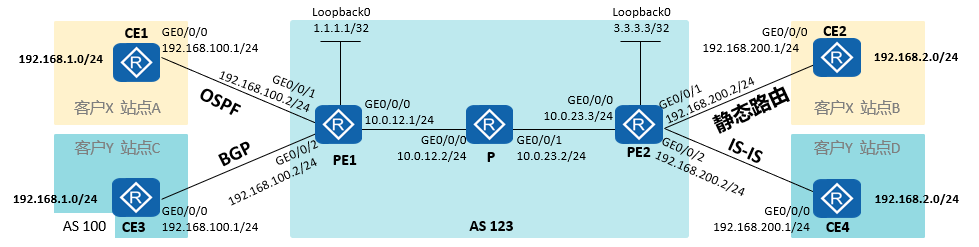
MPLS_VPN实验1
配置思路:
1.公网地址、IGP、LDP建立
2.PE连接站点,配置VPN实例接入,配置路由协议
3.PE与RR之间建立MP-IBGP邻居关系
4.在PE设备将站点路由信息引入到MP-BGP中公网配置
[AR2]isis
[AR2-isis-1]network-entity 49.0001.0000.0000.0002.00
[AR2-isis-1]is-level level-2
[AR2-isis-1]cost-style wide
[AR2]mpls lsr-id 2.2.2.2
[AR2]mpls
[AR2]mpls ldp
[AR2-GigabitEthernet0/0/1]ip ad 10.1.24.2 24
[AR2-GigabitEthernet0/0/1]isis enable
[AR2-GigabitEthernet0/0/1]mpls
[AR2-GigabitEthernet0/0/1]mpls ldp
[AR2-LoopBack0]ip ad 2.2.2.2 32
[AR2-LoopBack0]isis enable
[AR3]isis
[AR3-isis-1]network-entity 49.0001.0000.0000.0003.00
[AR3-isis-1]is-level level-2
[AR3-isis-1]cost-style wide
[AR3]mpls lsr-id 3.3.3.3
[AR3]mpls
[AR3]mpls ldp
[AR3-GigabitEthernet0/0/0]ip ad 10.1.34.3 24
[AR3-GigabitEthernet0/0/0]isis enable
[AR3-GigabitEthernet0/0/0]mpls
[AR3-GigabitEthernet0/0/0]mpls ldp
[AR3-LoopBack0]ip ad 3.3.3.3 32
[AR3-LoopBack0]isis enable
[AR4-isis-1]network-entity 49.0001.0000.0000.0004.00
[AR4-isis-1]is-level level-2
[AR4-isis-1]cost-style wide
[AR4]mpls lsr-id 4.4.4.4
[AR4]mpls
[AR4]mpls ldp
[AR4-GigabitEthernet0/0/0]ip ad 10.1.24.4 24
[AR4-GigabitEthernet0/0/0]isis enable
[AR4-GigabitEthernet0/0/0]mpls
[AR4-GigabitEthernet0/0/0]mpls ldp
[AR4-GigabitEthernet0/0/0]int gi 0/0/1
[AR4-GigabitEthernet0/0/1]ip ad 10.1.34.4 24
[AR4-GigabitEthernet0/0/1]isis enable
[AR4-GigabitEthernet0/0/1]mpls
[AR4-GigabitEthernet0/0/1]mpls ldp
[AR4-GigabitEthernet0/0/1]int gi 0/0/2
[AR4-GigabitEthernet0/0/2]ip ad 10.1.45.4 24
[AR4-GigabitEthernet0/0/2]isis enable
[AR4-GigabitEthernet0/0/2]mpls
[AR4-GigabitEthernet0/0/2]mpls ldp
[AR4-LoopBack0]ip ad 4.4.4.4 32
[AR4-LoopBack0]isis enable
[AR5]isis
[AR5-isis-1]network-entity 49.0001.0000.0000.0005.00
[AR5-isis-1]is-level level-2
[AR5-isis-1]cost-style wide
[AR5]mpls lsr-id 5.5.5.5
[AR5]mpls
[AR5]mpls ldp
[AR5-GigabitEthernet0/0/0]ip ad 10.1.45.5 24
[AR5-GigabitEthernet0/0/0]isis enable
[AR5-GigabitEthernet0/0/0]mpls
[AR5-GigabitEthernet0/0/0]mpls ldp
[AR5-LoopBack0]ip ad 5.5.5.5 32
[AR5-LoopBack0]isis enable PE连接CE配置
[AR1]ospf router-id 10.1.1.1
[AR1-ospf-1]area 0
[AR1-GigabitEthernet0/0/0]ip ad 10.1.12.1 24
[AR1-GigabitEthernet0/0/0]ospf enable area 0
[AR2]ip vpn-instance A
[AR2-vpn-instance-A]route-distinguisher 100:1
[AR2-vpn-instance-A-af-ipv4]vpn-target 1:1 直接配置RT值会同时配置IRT和ERT
IVT Assignment result:
Info: VPN-Target assignment is successful.
EVT Assignment result:
Info: VPN-Target assignment is successful.
[AR2]ospf router-id 10.2.2.2 vpn-instance A 在VPN实例A中建立OSPF邻居关系
[AR2-ospf-1]area 0
[AR2-GigabitEthernet0/0/0]ip binding vpn-instance A
[AR2-GigabitEthernet0/0/0]ip ad 10.1.12.2 24
[AR2-GigabitEthernet0/0/0]ospf enable area 0
[AR5]ip vpn-instance A
[AR5-vpn-instance-A]route-distinguisher 100:1
[AR5-vpn-instance-A-af-ipv4]vpn-target 1:1
[AR5]ospf router-id 10.5.5.5 vpn-instance A
[AR5-ospf-1]area 0
[AR5-GigabitEthernet0/0/1]ip binding vpn-instance A
[AR5-GigabitEthernet0/0/1]ip ad 10.1.56.5 24
[AR5-GigabitEthernet0/0/1]ospf enable area 0
[AR6]ospf router-id 10.6.6.6
[AR6-ospf-1-area-0.0.0.0]
[AR6-GigabitEthernet0/0/0]ip ad 10.1.56.6 24
[AR6-GigabitEthernet0/0/0]ospf enable area 0::: tip
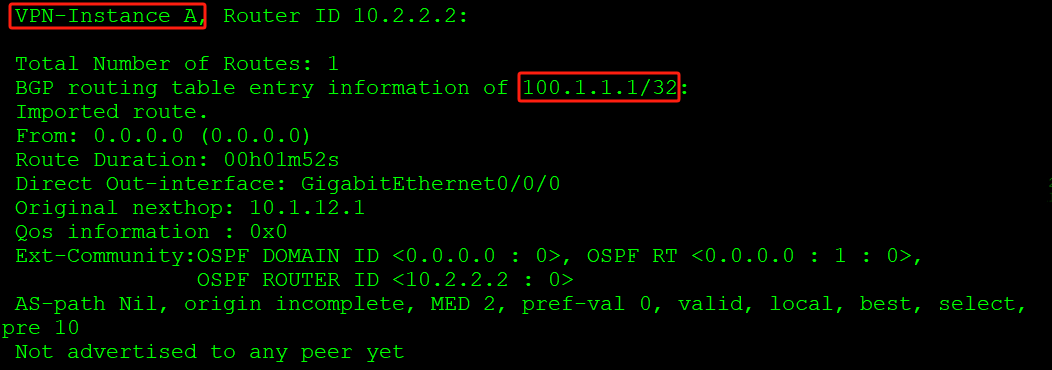
[AR1-LoopBack1]ip ad 100.1.1.1 32
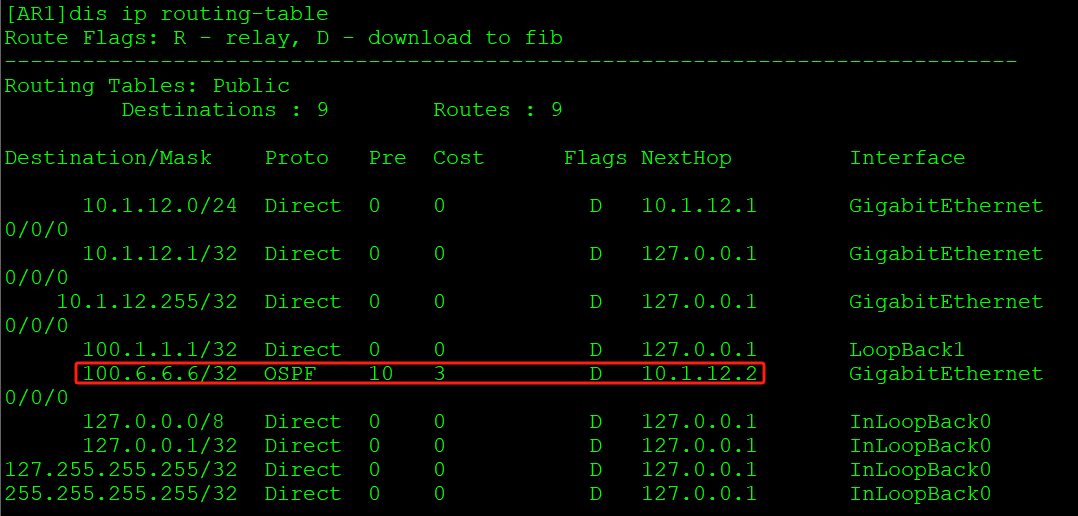
[AR1-LoopBack1]ospf enable area 0AR1在OSPF内通告环回口1,AR2可以查看到:
 站点路由通过OSPF传递,不会直接进入BGP VPNv4路由表。
:::
::: tip
RD值设置相等时,不同VPN实例的路由会出现在同一个VPNv4路由表中:
站点路由通过OSPF传递,不会直接进入BGP VPNv4路由表。
:::
::: tip
RD值设置相等时,不同VPN实例的路由会出现在同一个VPNv4路由表中:
MPLS VPN是三层VPN,同一个站点不能规划相同的网段。 :::
PE与RR建立MP-IBGP关系
[AR2]bgp 100
[AR2-bgp]router-id 10.2.2.2
[AR2-bgp]peer 3.3.3.3 as-number 100
[AR2-bgp]peer 3.3.3.3 connect-interface LoopBack 0
[AR2-bgp]dis th
[V200R003C00]
#
bgp 100
router-id 10.2.2.2
peer 3.3.3.3 as-number 100
peer 3.3.3.3 connect-interface LoopBack0
#
ipv4-family unicast
undo synchronization
peer 3.3.3.3 enable BGP默认在IP v4地址族下使能
#
return
[AR2-bgp]undo peer 3.3.3.3 enable
[AR2-bgp]ipv4-family vpnv4 在IP v4 VPNv4地址族下使能
[AR2-bgp-af-vpnv4]peer 3.3.3.3 enable
AR5的配置和AR2类似
[AR5]bgp 100
[AR5-bgp]router-id 10.5.5.5
[AR5-bgp]peer 3.3.3.3 as-number 100
[AR5-bgp]peer 3.3.3.3 connect-interface LoopBack 0
[AR5-bgp]undo peer 3.3.3.3 enable
[AR5-bgp]ipv4-family vpnv4
[AR5-bgp-af-vpnv4]peer 3.3.3.3 enable
反射器AR3配置,建立IBGP邻居关系
[AR3]bgp 100
[AR3-bgp]router-id 10.3.3.3
[AR3-bgp]peer 2.2.2.2 as-number 100
[AR3-bgp]peer 2.2.2.2 connect-interface LoopBack 0
[AR3-bgp]undo peer 2.2.2.2 enable
[AR3-bgp]peer 5.5.5.5 as-number 100
[AR3-bgp]peer 5.5.5.5 connect-interface LoopBack 0
[AR3-bgp]undo peer 5.5.5.5 enable
[AR3-bgp]ipv4-family vpnv4
[AR3-bgp-af-vpnv4]peer 2.2.2.2 enable
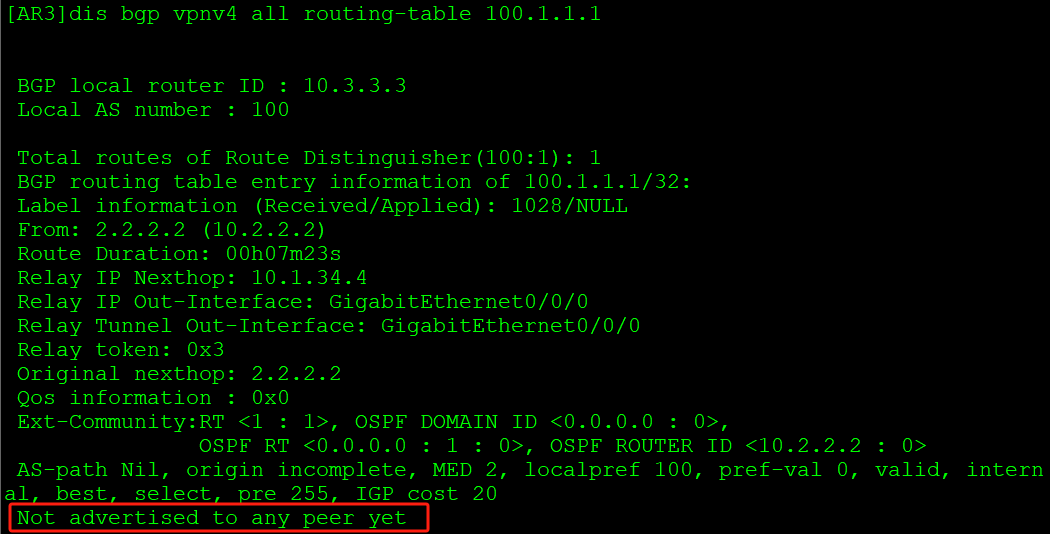
[AR3-bgp-af-vpnv4]peer 5.5.5.5 enable ::: tip PE设备AR2学习到的100.1.1.1绑定了VPN实例,需要在VPN实例下做引入。 :::
PE设备引入CE设备的路由
[AR2]bgp 100
[AR2-bgp]ipv4-family vpn-instance A 进入VPN实例
[AR2-bgp-A]import-route ospf 1 在VPN实例下做引入::: warning
流程:站点CE设备发送的路由通过OSPF,PE设备需要引入到BGP的VPN实例,再转为VPNv4路由。
VPN实例的路由相对于公网路由是单独的,不能在BGP视图下直接配置引入。
:::
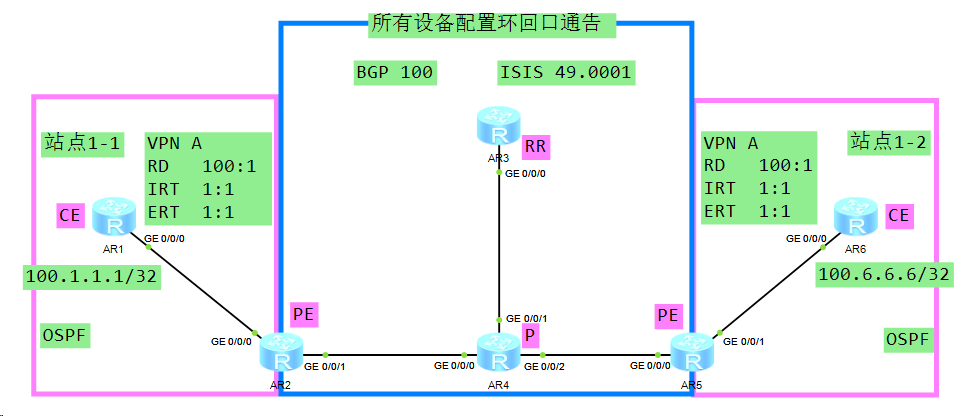
 ::: tip
::: tip
AR2的VPN实例A中过滤不需要的路由10.1.12.0/24
[AR2]acl 2000
[AR2-acl-basic-2000]rule 5 permit source 100.1.1.1 0 ACL默认拒绝
[AR2]route-policy OSPF_TO_BGP permit node 10
[AR2-route-policy]if-match acl 2000
[AR2]bgp 100
[AR2-bgp]ipv4-family vpn-instance A 引入到VPN实例
[AR2-bgp-A]import-route ospf 1 route-policy OSPF_TO_BGP  :::
:::

 如上,100.1.1.1的路由先引入VPN实例路由表中,再转换成VPNv4路由,携带出RT值和私网标签,通告给3.3.3.3。
如上,100.1.1.1的路由先引入VPN实例路由表中,再转换成VPNv4路由,携带出RT值和私网标签,通告给3.3.3.3。
::: warning
没有VPN实例的设备接收到私网路由时默认过滤所有:
如果公网中存在RR设备,需要在RR设备上的BGP IP v4 VPNv4地址族下关闭policy vpn-target,以便于RR接收私网路由。 PE设备不需要关闭该策略,原因是PE设备上存在RT值,IRT匹配优先于策略接收路由信息。 即存在IRT,优先被IRT匹配接收,不存在IRT,就会被策略过滤。 :::
[AR3]bgp 100
[AR3-bgp]ipv4-family vpnv4
[AR3-bgp-af-vpnv4]undo policy vpn-target 关闭过滤私网路由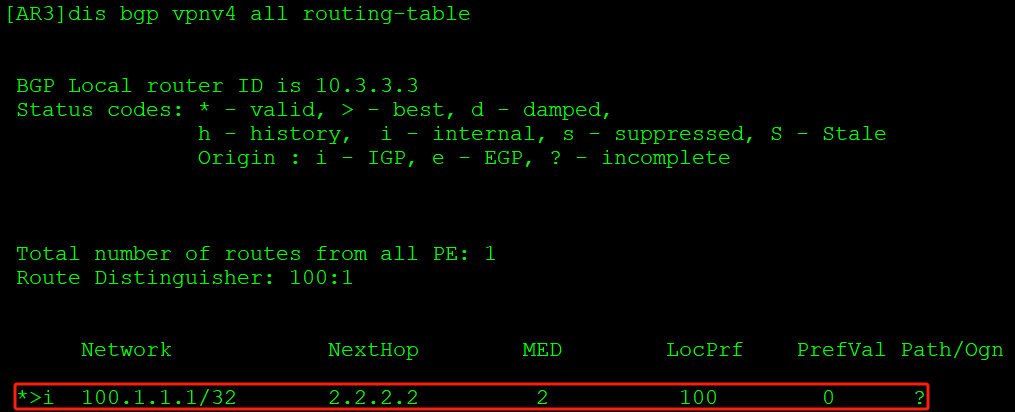
 如上,AR3没有通告给其他邻居的原因是配置RR时没有指定客户端,出现IBGP水平分割现象。
如上,AR3没有通告给其他邻居的原因是配置RR时没有指定客户端,出现IBGP水平分割现象。
[AR3-bgp-af-vpnv4]peer 2.2.2.2 reflect-client 反射器指定客户端
[AR3-bgp-af-vpnv4]peer 5.5.5.5 reflect-client 反射器指定客户端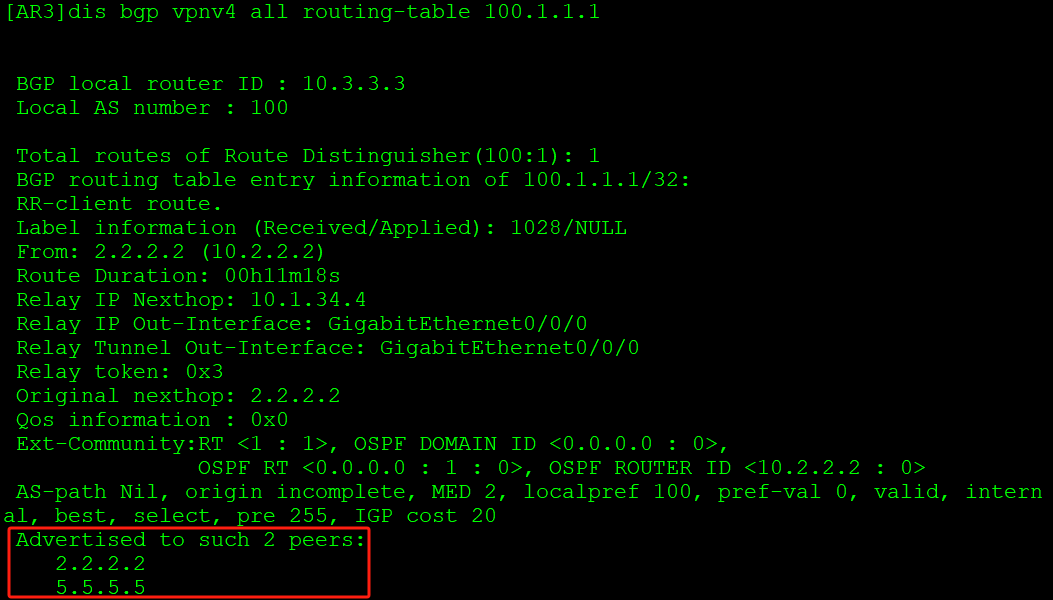 ::: tip
上述通告回2.2.2.2可能存在问题,原因是该路由从2.2.2.2发来,不应传递回去。但由于BGP存在防环规则,传回2.2.2.2也不会出现任何问题。
:::
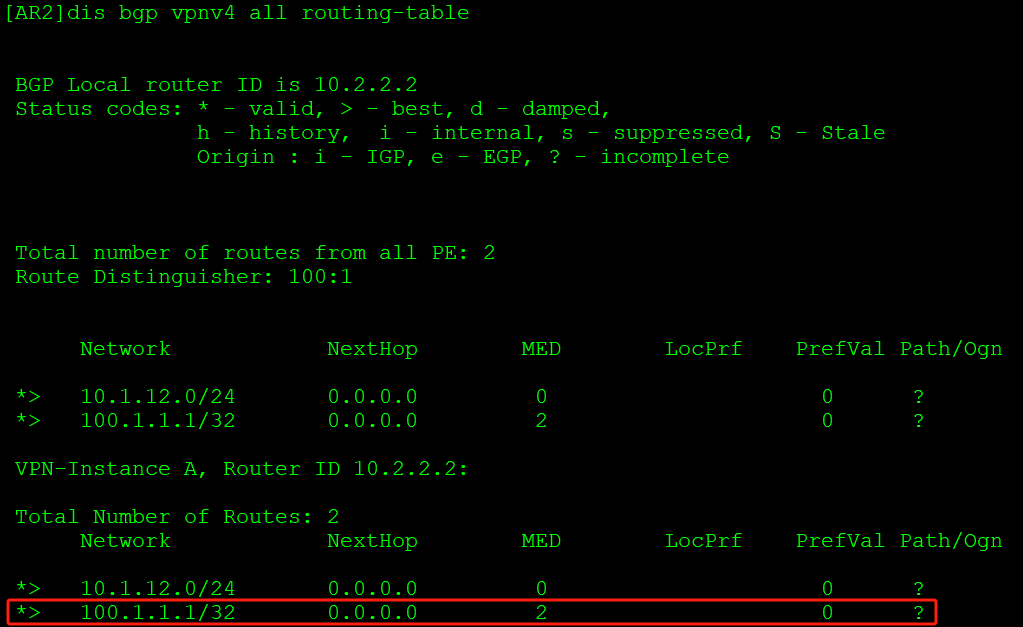
AR5学习到100.1.1.1的VPNv4路由,并转换到VPN实例路由表中:
::: tip
上述通告回2.2.2.2可能存在问题,原因是该路由从2.2.2.2发来,不应传递回去。但由于BGP存在防环规则,传回2.2.2.2也不会出现任何问题。
:::
AR5学习到100.1.1.1的VPNv4路由,并转换到VPN实例路由表中:
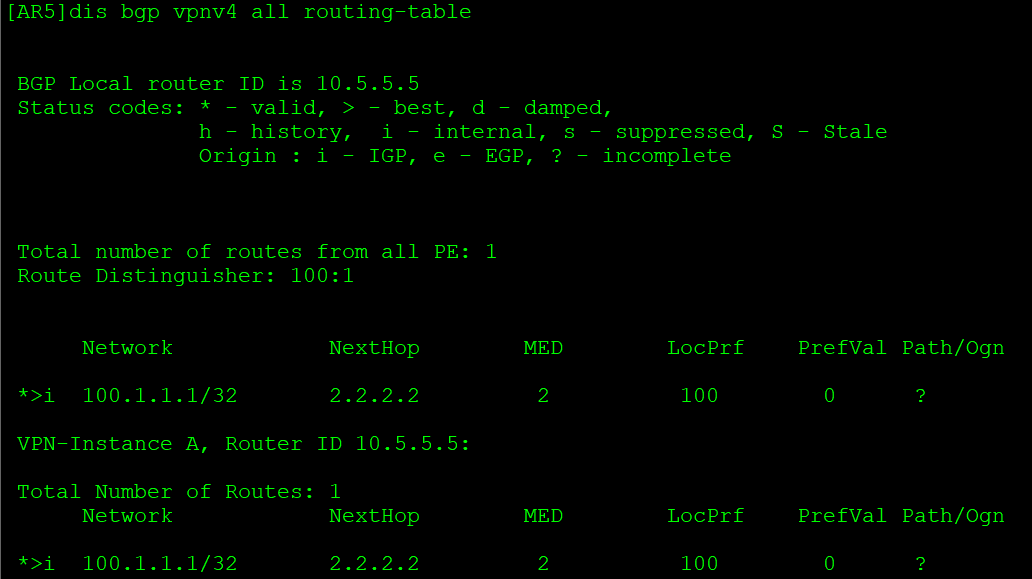
CE设备引入PE设备的路由,即BGP(EGP)到IGP引入
[AR5]ospf
[AR5-ospf-1]import-route bgp 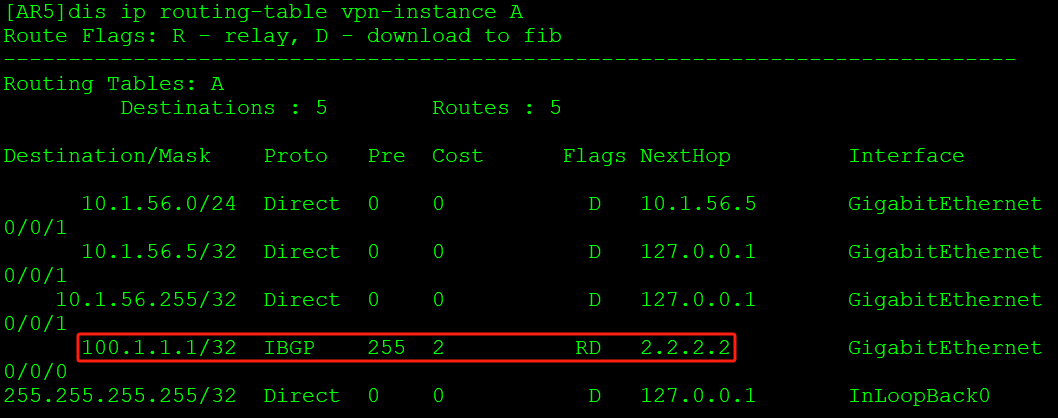 即将如上AR5的IBGP路由引入到OSPF中。
即将如上AR5的IBGP路由引入到OSPF中。
AR6接收到AR1通告的路由:
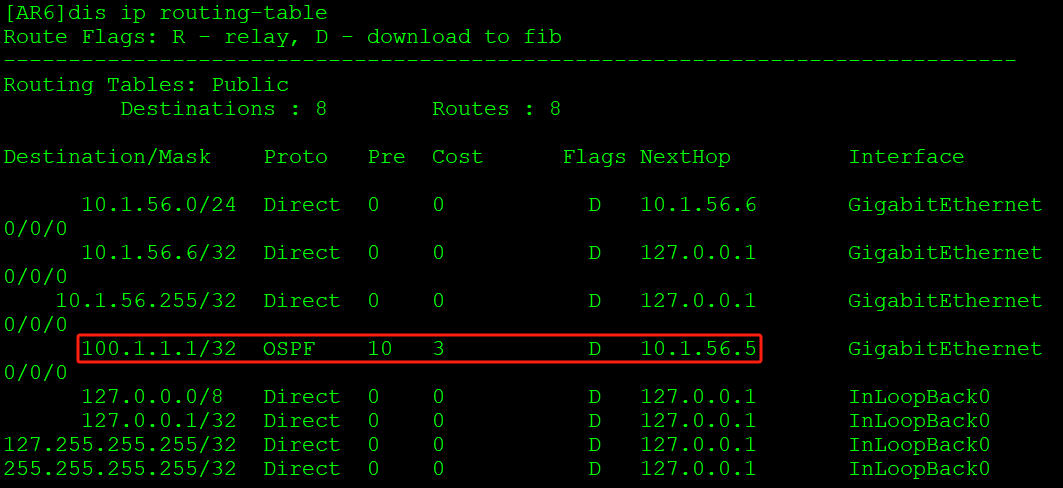
AR6配置通告路由,传递给AR1
[AR6-LoopBack1]ip ad 100.6.6.6 32
[AR6-LoopBack1]ospf enable area 0
AR5将OSPF做策略过滤引入BGP
[AR5]acl 2000
[AR5-acl-basic-2000]rule 5 permit source 100.6.6.6 0
[AR5]route-policy OSPF_TO_BGP permit node 10
[AR5-route-policy]if-match acl 2000
[AR5]bgp 100
[AR5-bgp]ipv4-family vpn-instance A
[AR5-bgp-A]import-route ospf 1 route-policy OSPF_TO_BGP
AR2将BGP引入OSPF
[AR2]ospf
[AR2-ospf-1]import-route bgp AR1接收到AR6通告的路由:
MPLS_VPN实验1总结
AR1访问AR6数据转发平面流程:
- 数据发送到AR2
AR2从绑定VPN实例的接口收到,查看VPN实例转发表:
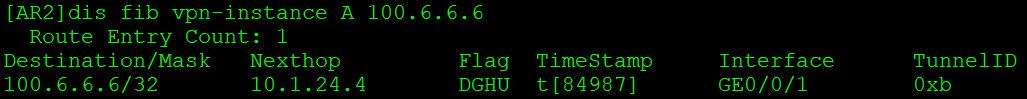 TunnelID不为0,表示通过隧道转发。
TunnelID不为0,表示通过隧道转发。
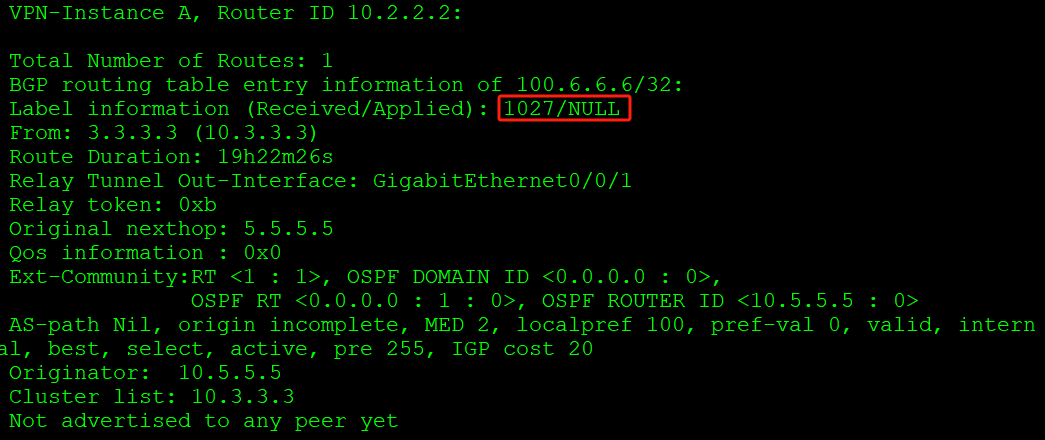
查看私网标签信息(通过VPNv4路由表中查看对应路由的明细信息),私网标签1027:
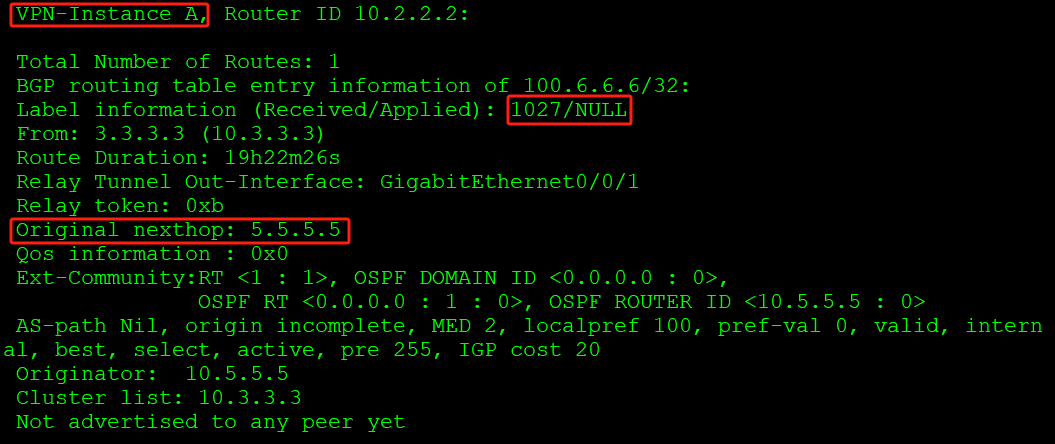 如上起源下一跳为5.5.5.5,通过FIB表查询转发:
如上起源下一跳为5.5.5.5,通过FIB表查询转发:
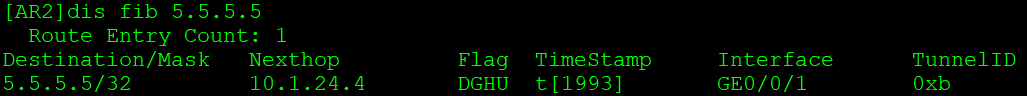 TunnelID不为0,表示通过隧道转发。
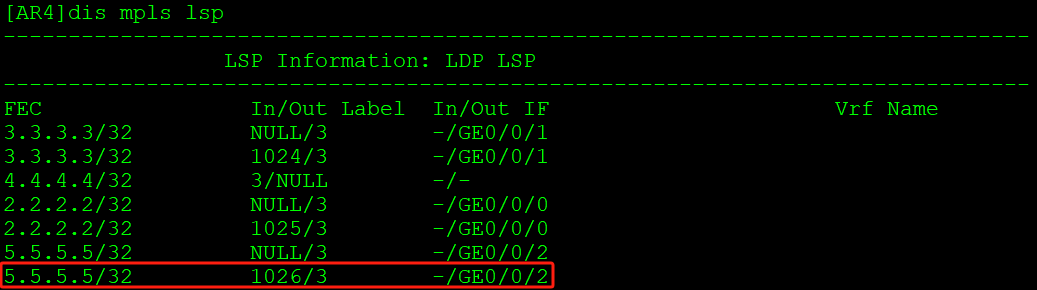
去往5.5.5.5走公网LSP隧道,入节点封装标签1026:
TunnelID不为0,表示通过隧道转发。
去往5.5.5.5走公网LSP隧道,入节点封装标签1026:
 2. 数据发送到AR4
AR2通过接口GE0/0/1发出到AR4,AR4将该数据封装标签3,从GE0/0/2接口转发,弹出公网标签:
2. 数据发送到AR4
AR2通过接口GE0/0/1发出到AR4,AR4将该数据封装标签3,从GE0/0/2接口转发,弹出公网标签:
 3. 数据发送到AR5
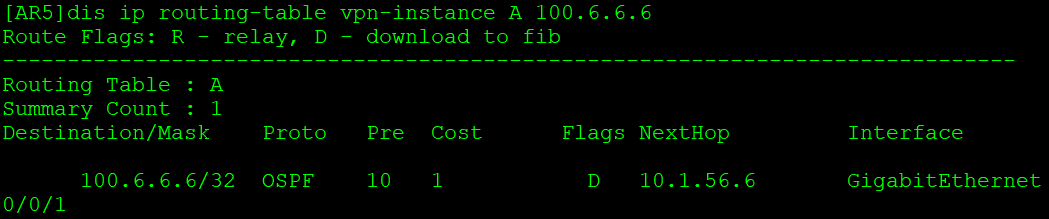
AR5收到后,根据私网标签送入VPN站点:
3. 数据发送到AR5
AR5收到后,根据私网标签送入VPN站点:
如上,AR3做旁挂,RR不需要做数据平面转发,只做路由控制转发,节省了设备资源。
::: warning
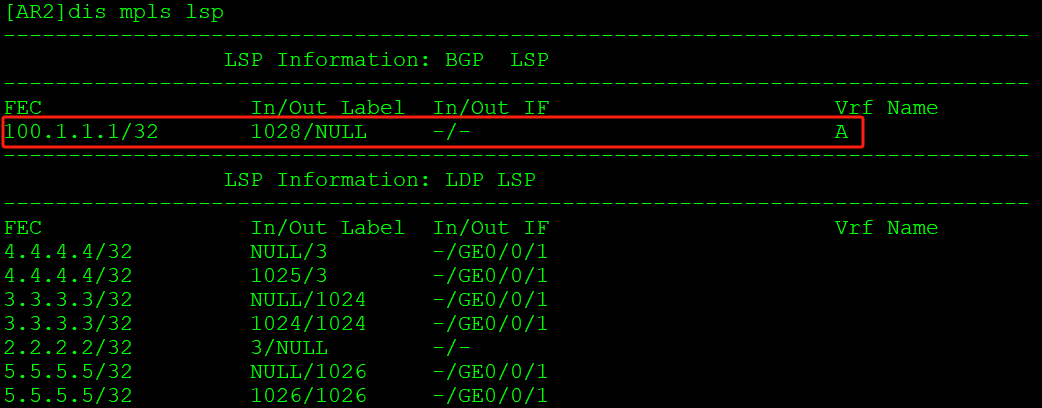
MPLS_LSP表中只会保留自身私网BGP_LSP信息:
 需要查看VPNv4路由表对应路由的明细信息查看LSP标签信息:
需要查看VPNv4路由表对应路由的明细信息查看LSP标签信息:
 :::
::: tip
设备查询FIB表时,先查询FIB VPN实例表,再查询FIB表。
:::
::: tip
设备查询FIB表时,先查询FIB VPN实例表,再查询FIB表。
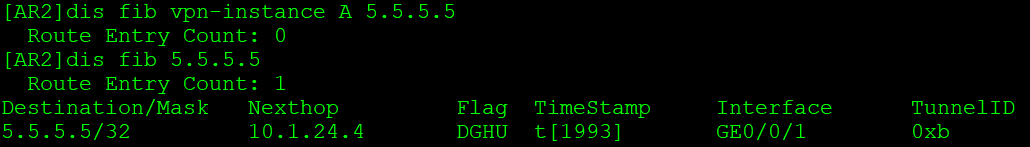 :::
AR1重新通告100.1.1.1:
:::
AR1重新通告100.1.1.1:
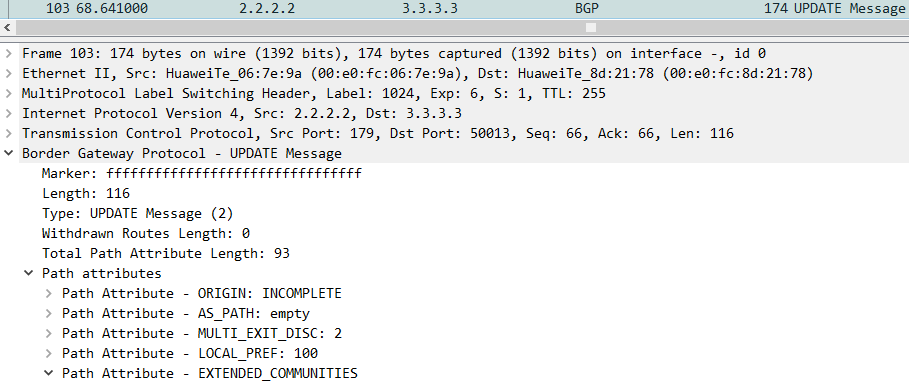

AR1 100.1.1.1访问AR6 100.6.6.6,AR1 GE0/0/1抓包:
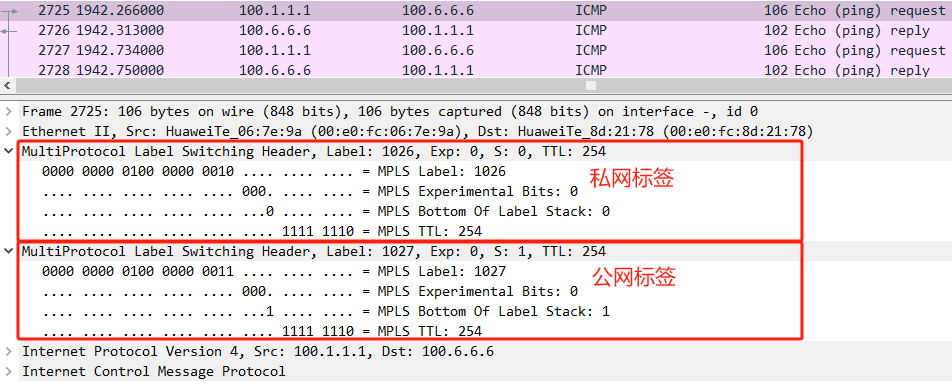 ::: tip
公网标签由LDP分配,私网标签由MP-BGP分配。都通过MPLS转发。
如上拓扑私网隧道AR2-AR5,公网隧道AR2-AR4,AR4-AR5。
:::
::: warning
AR3作为RR设备,如果RR设备旁挂,可以不开启MPLS、LDP等协议,RR只作为控制平面传递路由,不需要做数据平面转发。
即如上拓扑,AR3和AR4连接AR3的端口可以不做MPLS配置。
:::
::: tip
公网标签由LDP分配,私网标签由MP-BGP分配。都通过MPLS转发。
如上拓扑私网隧道AR2-AR5,公网隧道AR2-AR4,AR4-AR5。
:::
::: warning
AR3作为RR设备,如果RR设备旁挂,可以不开启MPLS、LDP等协议,RR只作为控制平面传递路由,不需要做数据平面转发。
即如上拓扑,AR3和AR4连接AR3的端口可以不做MPLS配置。
:::
MPLS_VPN实验2
实验1的基础上,连接两台设备加入公网:
两台CE设备配置接入公网
[AR2]ip vpn-instance B
[AR2-vpn-instance-B]route-distinguisher 200:1
[AR2-vpn-instance-B-af-ipv4]vpn-target 2:2
[AR2]ospf 2 router-id 10.2.2.2 vpn-instance B OSPF一个进程只能绑定一个VPN实例
[AR2-ospf-2]area 0
[AR2-GigabitEthernet0/0/2]ip binding vpn-instance B
[AR2-GigabitEthernet0/0/2]ip ad 10.1.27.2 24
[AR2-GigabitEthernet0/0/2]ospf enable 2 area 0 使用OSPF进程2
[AR7]ospf router-id 10.7.7.7
[AR7-ospf-1]area 0
[AR7-GigabitEthernet0/0/0]ip ad 10.1.27.7 24
[AR7-GigabitEthernet0/0/0]ospf enable area 0 使用OSPF进程1
[AR5]ip vpn-instance B
[AR5-vpn-instance-B]route-distinguisher 200:1
[AR5-vpn-instance-B-af-ipv4]vpn-target 2:2
[AR5]ospf 2 router-id 10.5.5.5 vpn-instance B
[AR5-ospf-2]area 0
[AR5-GigabitEthernet0/0/2]ip binding vpn-instance B
[AR5-GigabitEthernet0/0/2]ip ad 10.1.58.5 24
[AR5-GigabitEthernet0/0/2]ospf enable 2 area 0
[AR8]ospf 2 router-id 10.8.8.8
[AR8-ospf-2]area 0
[AR8-GigabitEthernet0/0/0]ip ad 10.1.58.8 24
[AR8-GigabitEthernet0/0/0]ospf enable 2 area 0::: tip
AR2和AR7两端四年进程不同不影响邻居建立,现网中为了统一规划一般设置成相同进程。
:::
AR7通告路由100.7.7.7给AR2:
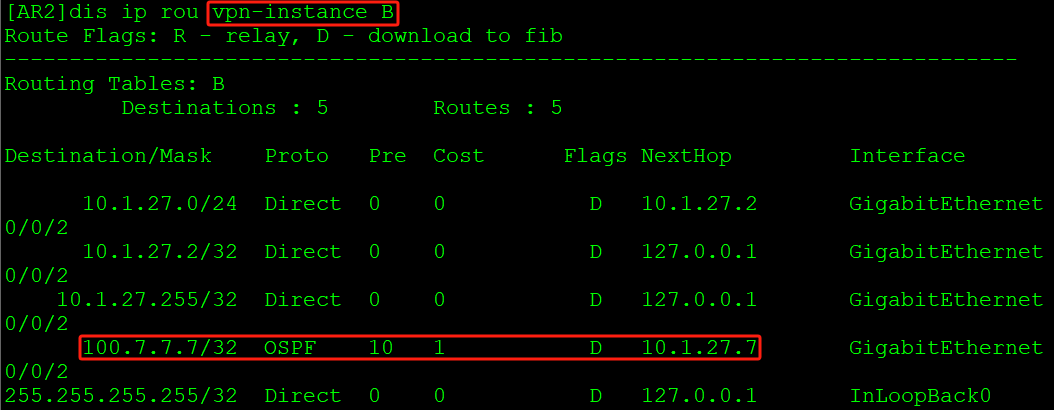 AR2 VPNv4表中没有VPN实例B的路由:
AR2 VPNv4表中没有VPN实例B的路由:

VPN实例B中引入AR7通告在OSPF进程2的路由
[AR2]bgp 100
[AR2-bgp]ipv4-family vpn-instance B
[AR2-bgp-B]import-route ospf 2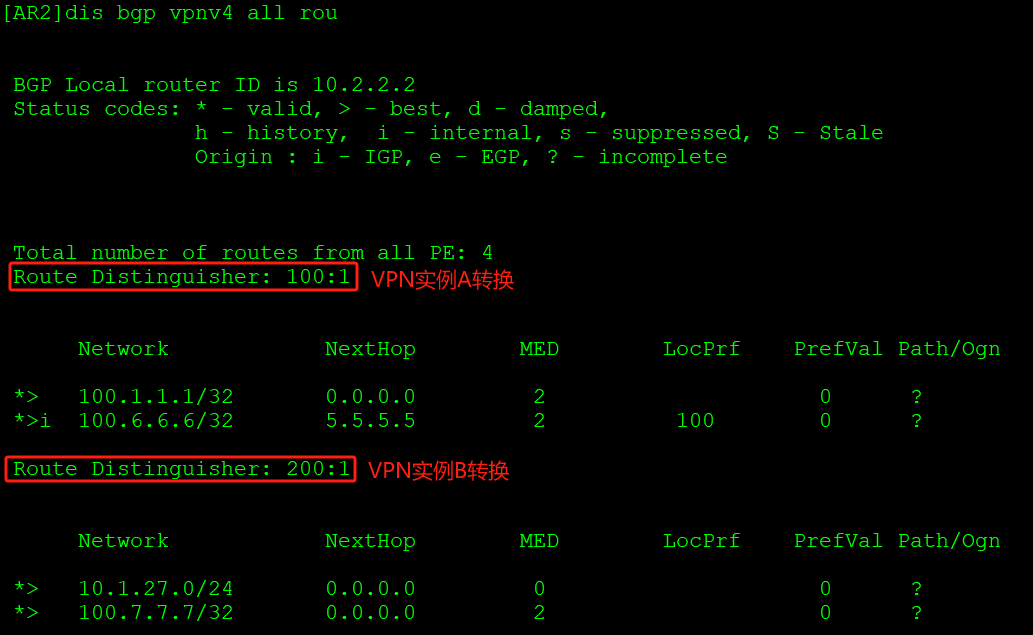
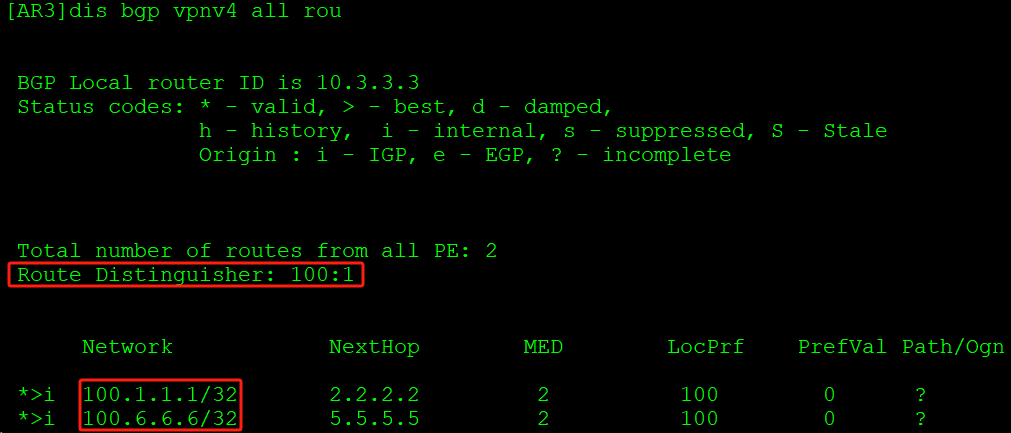
 AR3的VPNv4路由表中出现两个RD值的路由:
AR3的VPNv4路由表中出现两个RD值的路由:
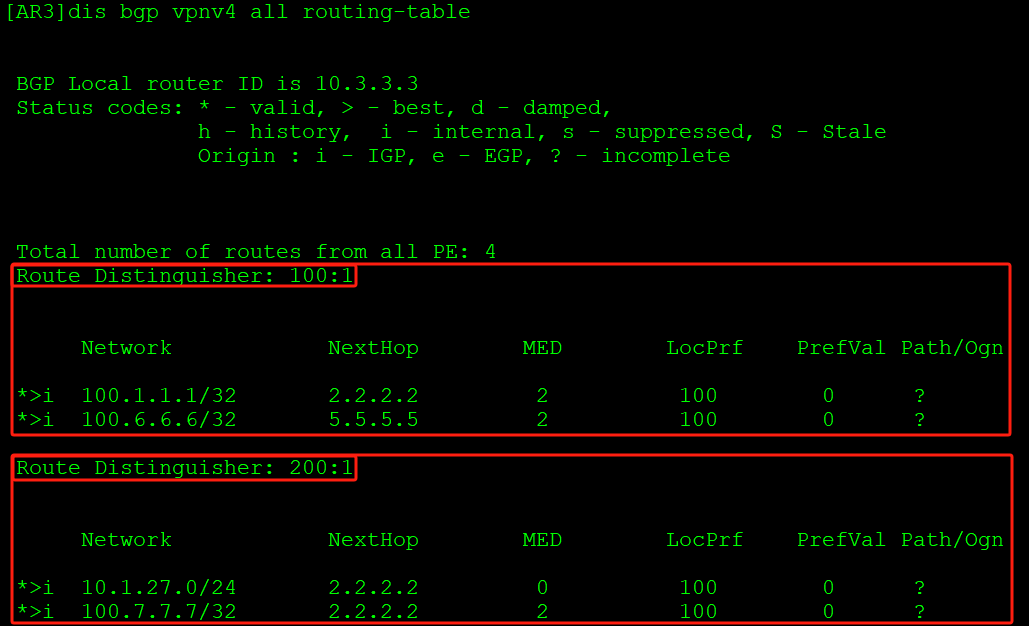 AR5收到VPNv4路由后转换成VPN实例路由表:
AR5收到VPNv4路由后转换成VPN实例路由表:
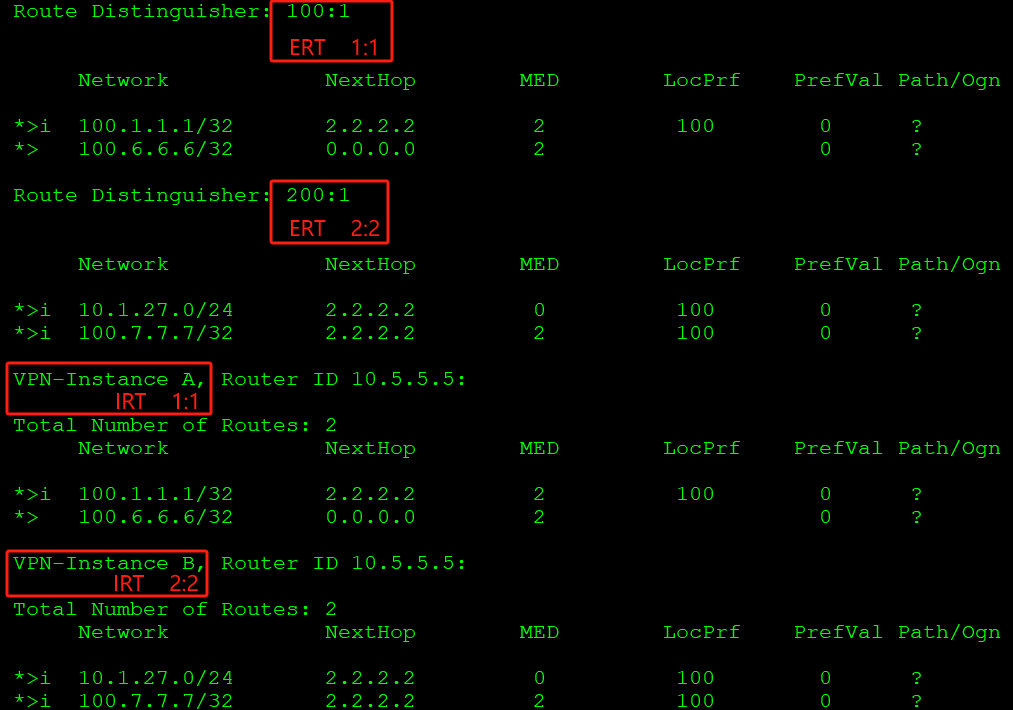 ::: warning
VPNv4路由转换到VPN实例路由表,通过ERT匹配IRT实现。
:::
如上,RD值100:1的VPNv4路由携带ERT值1:1,匹配VPN实例A的IRT值1:1;RD值200:1的VPNv4路由携带ERT值2:2,匹配VPN实例B的IRT值2:2,将不同RD值的VPNv4路由转换到对应的VPN实例路由表中。
::: warning
VPNv4路由转换到VPN实例路由表,通过ERT匹配IRT实现。
:::
如上,RD值100:1的VPNv4路由携带ERT值1:1,匹配VPN实例A的IRT值1:1;RD值200:1的VPNv4路由携带ERT值2:2,匹配VPN实例B的IRT值2:2,将不同RD值的VPNv4路由转换到对应的VPN实例路由表中。
将路由从BGP引入OSPF(路由引入到站点)
[AR5]ospf 2 在OSPF协议连接站点的进程视图下
[AR5-ospf-2]import-route bgp ::: warning 上述引入BGP不会引入100.1.1.1等,原因是OSPF进程2对应VPN实例B:
:::
AR8收到AR7通告的路由:
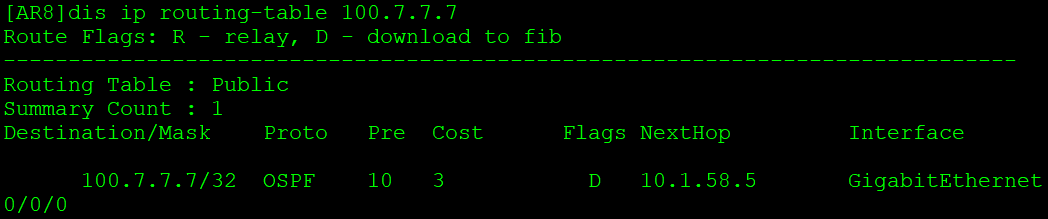
VPN实例B中引入AR8通告在OSPF进程2的路由
[AR5]bgp 100
[AR5-bgp]ipv4-family vpn-instance B
[AR5-bgp-B]import-route ospf 2通过反射器传递给对端AR2,AR2的VPN实例B可以收到对应路由:
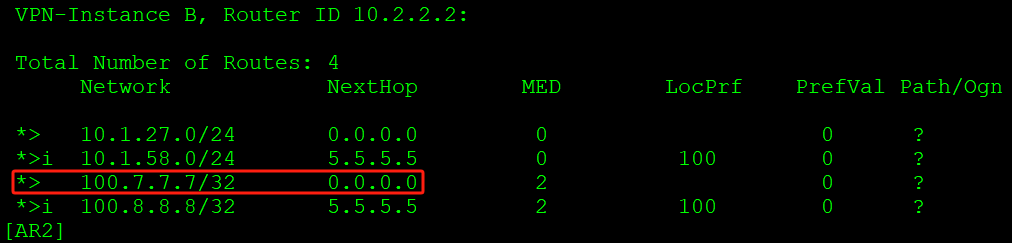
将路由从BGP引入OSPF(路由引入到站点)
[AR2]ospf 2
[AR2-ospf-2]import-route bgp 站点设备AR7收到AR8通告的路由:
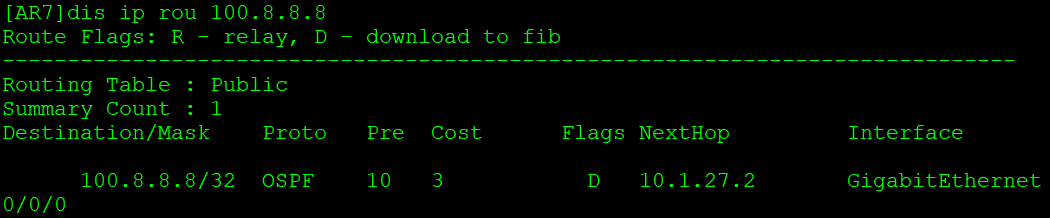
MPLS_VPN实验3
实验2的基础上,连接1台设备加入公网:
[AR4-GigabitEthernet2/0/0]ip ad 10.1.49.4 24
[AR4-GigabitEthernet2/0/0]isis enable
[AR4-GigabitEthernet2/0/0]mpls
[AR4-GigabitEthernet2/0/0]mpls ldp
[AR9]isis
[AR9-isis-1]network-entity 49.0001.0000.0000.0009.00
[AR9-isis-1]is-level level-2
[AR9-isis-1]cost-style wide
[AR9-GigabitEthernet0/0/0]ip ad 10.1.49.9 24
[AR9-GigabitEthernet0/0/0]isis enable
[AR9-LoopBack0]ip ad 9.9.9.9 32
[AR9-LoopBack0]isis enable
[AR9]mpls lsr-id 9.9.9.9
[AR9]mpls
[AR9-mpls]mpls ldp
[AR9-GigabitEthernet0/0/0]mpls
[AR9-GigabitEthernet0/0/0]mpls ldp
[AR9]ip vpn-instance C
[AR9-vpn-instance-C]route-distinguisher 300:1
[AR9-LoopBack1]ip binding vpn-instance C
[AR9-LoopBack1]ip ad 100.9.9.9 32
AR9和AR3建立BGP邻居
[AR9]bgp 100
[AR9-bgp]peer 3.3.3.3 as-number 100
[AR9-bgp]peer 3.3.3.3 connect-interface LoopBack 0
[AR9-bgp]undo peer 3.3.3.3 enable
[AR9-bgp]ipv4-family vpnv4
[AR9-bgp-af-vpnv4]peer 3.3.3.3 enable
[AR3]bgp 100
[AR3-bgp]peer 9.9.9.9 as-number 100
[AR3-bgp]peer 9.9.9.9 connect-interface LoopBack 0
[AR3-bgp]undo peer 9.9.9.9 enable
[AR3-bgp]ipv4-family vpnv4
[AR3-bgp-af-vpnv4]peer 9.9.9.9 enable
[AR3-bgp-af-vpnv4]peer 9.9.9.9 reflect-client 查看AR3和AR9的VPNv4邻居建立:
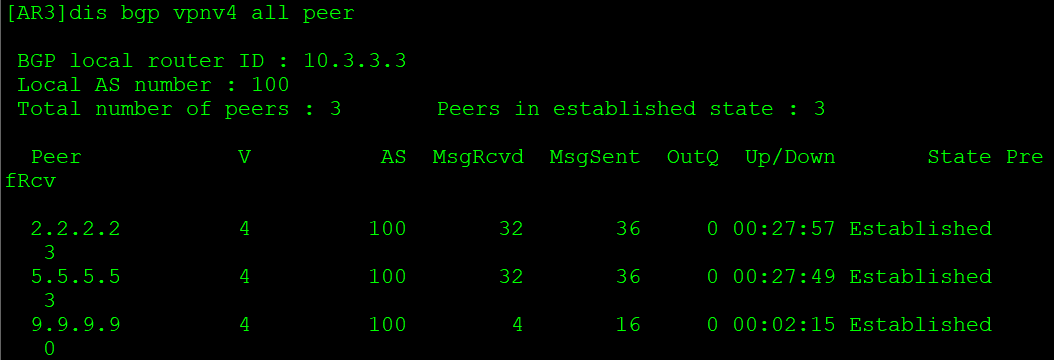 路由通告给AR9:
路由通告给AR9:
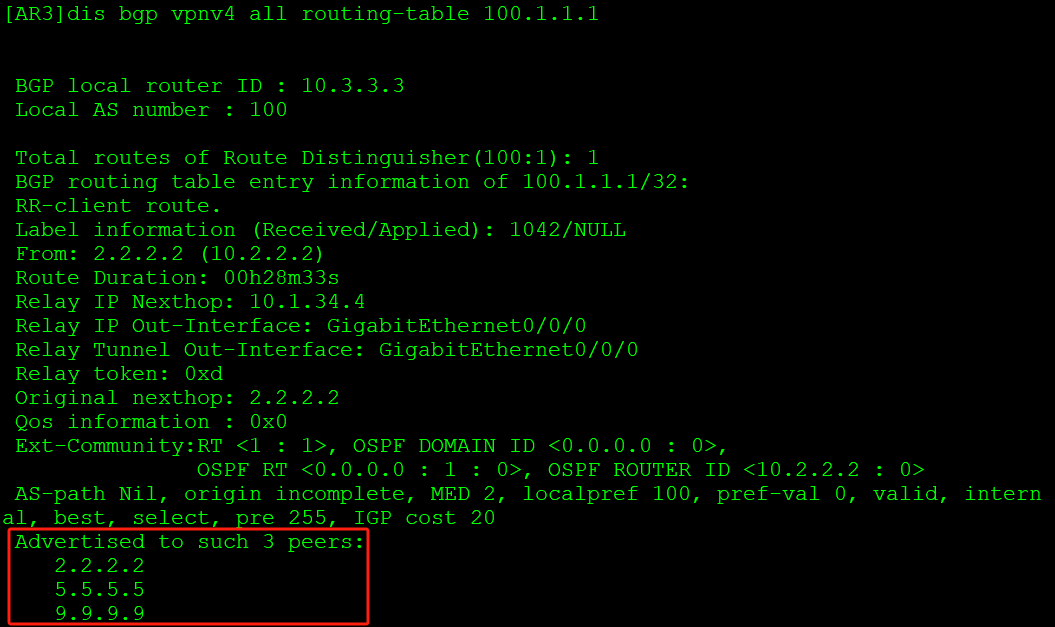
AR9上没有配置RT值,手动取消过滤接收私网路由
[AR9-bgp]ipv4-family vpnv4
[AR9-bgp-af-vpnv4]undo policy vpn-target AR9可以收到私网路由,但不能加入VPN实例:
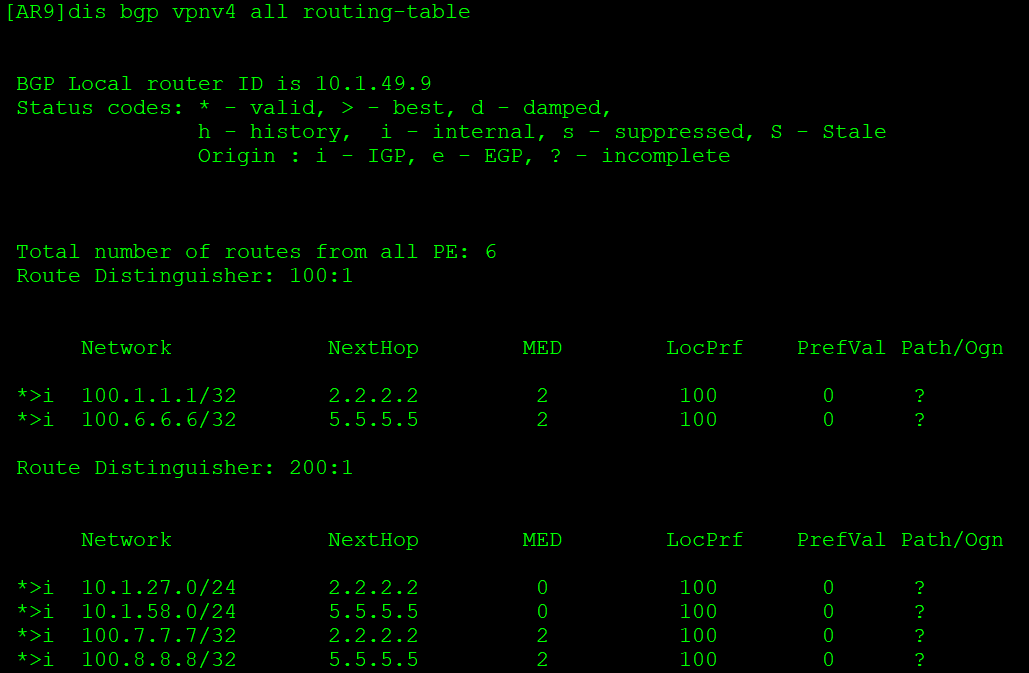
AR9作为PE设备,应通过设置RT值接收私网路由
[AR9]bgp 100
[AR9-bgp]ipv4-family vpnv4
[AR9-bgp-af-vpnv4]policy vpn-target
[AR9-vpn-instance-C]vpn-target 1:1 2:2 import-extcommunity 设置IRT对应接收VPN实例A、B的ERT
[AR9-vpn-instance-C]dis th
[V200R003C00]
#
ip vpn-instance C
ipv4-family
route-distinguisher 300:1
vpn-target 1:1 2:2 import-extcommunity
#
return
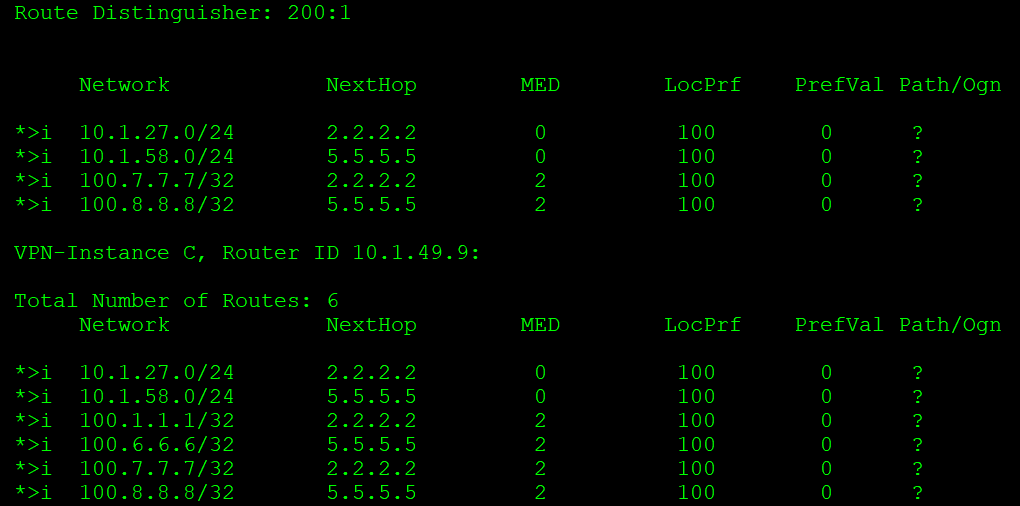 如上,由于VPN实例C中的IRT包含两个RD值的路由的ERT,都会接收到VPN实例C中。
如上,由于VPN实例C中的IRT包含两个RD值的路由的ERT,都会接收到VPN实例C中。
过滤VPN实例C中非环回口路由
[AR9]ip ip-prefix host index 10 permit 100.0.0.0 8 greater-equal 32 less-equal 32 在100.0.0.0/8网段内,只匹配主机路由(32为掩码)
[AR9]route-policy host permit node 10
[AR9-route-policy]if-match ip-prefix host
[AR9]bgp 100
[AR9-bgp]ipv4-family vpnv4
[AR9-bgp-af-vpnv4]peer 3.3.3.3 route-policy host import AR3上做过滤时为export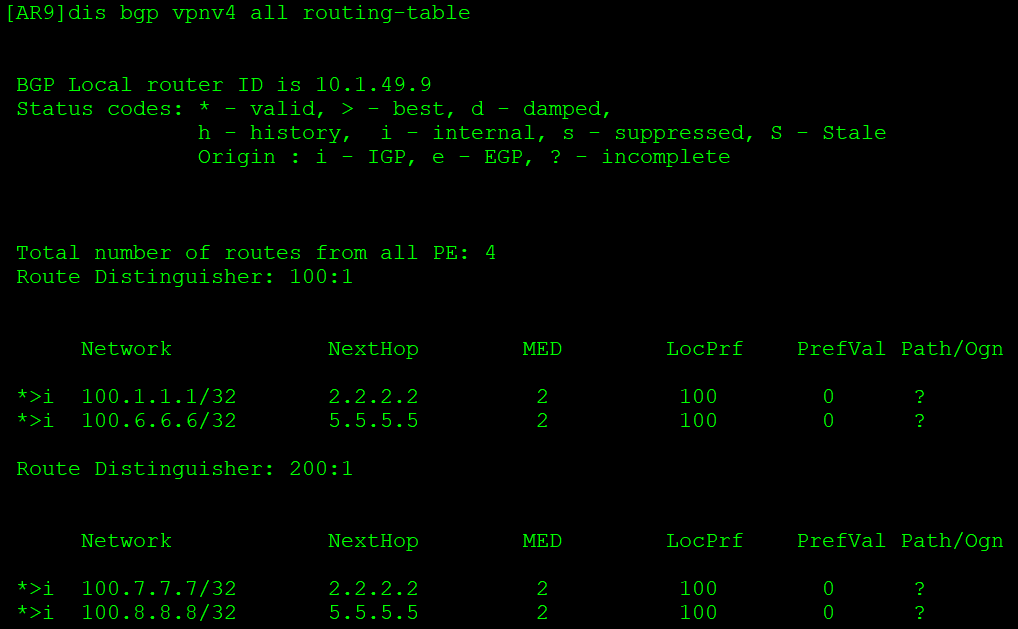
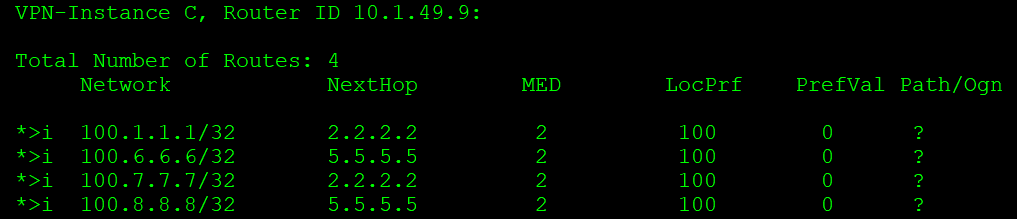 如上,VPN实例B的24位路由被过滤,即AR3传来的VPNv4路由被过滤,转换到VPN实例C的路由中就只有主机路由。(实验1中AR2和AR5做了ACL 2000过滤了非通告路由网段。)
如果AR9下部分站点需要接收非主机路由,部分站点不需要接收非主机路由,上述过滤VPNv4路由的操作无法实现。
如上,VPN实例B的24位路由被过滤,即AR3传来的VPNv4路由被过滤,转换到VPN实例C的路由中就只有主机路由。(实验1中AR2和AR5做了ACL 2000过滤了非通告路由网段。)
如果AR9下部分站点需要接收非主机路由,部分站点不需要接收非主机路由,上述过滤VPNv4路由的操作无法实现。
[AR9-bgp]ipv4-family vpnv4
[AR9-bgp-af-vpnv4]undo peer 3.3.3.3 route-policy host import
[AR9]ip vpn-instance C
[AR9-vpn-instance-C]import route-policy host 在VPN实例内引入路由策略
 如上,在不需要非主机路由的站点实例C下调用路由策略过滤,不影响设备接收VPNv4路由,其他站点需要接收非主机路由时,VPNv4路由可以正常转换成该站点的VPN实例路由。
::: warning
VPNv4视图下配置过滤影响全局,VPN实例视图下配置过滤仅影响该站点。
:::
如上,在不需要非主机路由的站点实例C下调用路由策略过滤,不影响设备接收VPNv4路由,其他站点需要接收非主机路由时,VPNv4路由可以正常转换成该站点的VPN实例路由。
::: warning
VPNv4视图下配置过滤影响全局,VPN实例视图下配置过滤仅影响该站点。
:::
MPLS_VPN实验4
Hub-Spoke组网即企业总部 + 分支,一般由企业总部和数据中心作为Hub站点,企业各分支作为Spoke站点,通过WAN集中访问部署在总部或者数据中心站点的服务器应用;同时,企业的分支之间如果需要互通,也经过Hub站点中转。
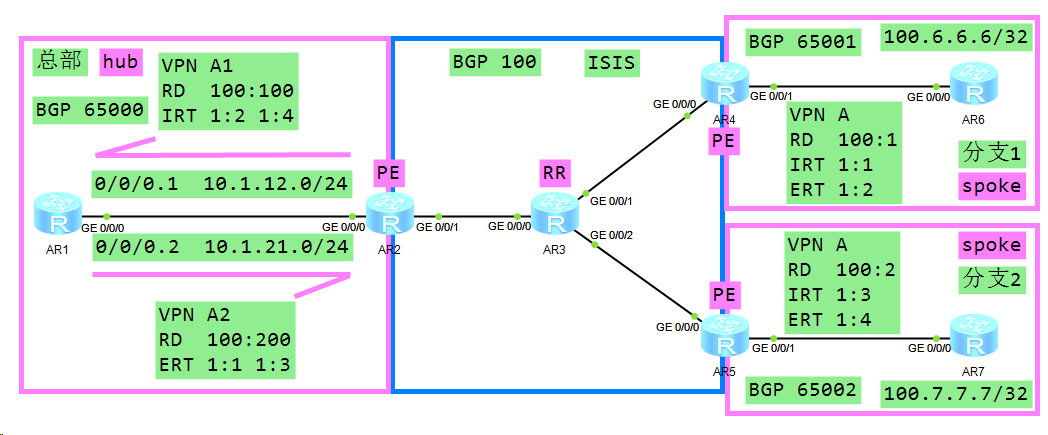 上述拓扑如果AR7通告7.7.7.7的路由,AR1收到后需要在AR1和AR2之间再建立一条通道(再建立一个邻居关系)或者建立子接口(单臂路由)。
::: warning
IGP水平分割:从某个接口学习到的路由信息不会从该接口通告出去。
BGP水平分割:从IBGP邻居学到的路由信息不会向其他IBGP邻居转发。
:::
上述拓扑如果AR7通告7.7.7.7的路由,AR1收到后需要在AR1和AR2之间再建立一条通道(再建立一个邻居关系)或者建立子接口(单臂路由)。
::: warning
IGP水平分割:从某个接口学习到的路由信息不会从该接口通告出去。
BGP水平分割:从IBGP邻居学到的路由信息不会向其他IBGP邻居转发。
:::
组网思路:
分支AR7通告路由,走总部AR1转发
AR1和AR2建立两个邻居关系,AR2上使用两个VPN实例,一个VPN实例将路由发送到AR1,另一个VPN实例接收AR1发来的路由
AR1将收到的路由转发到AR4、AR5,满足AR6和AR5下其他分支站点接收该路由的要求公网配置
[AR2]isis
[AR2-isis-1]network-entity 49.0001.0000.0000.0002.00
[AR2-isis-1]is-level level-2
[AR2-isis-1]cost-style wide
[AR2]mpls lsr-id 2.2.2.2
[AR2]mpls
[AR2]mpls ldp
[AR2-GigabitEthernet0/0/1]ip ad 10.1.23.2 24
[AR2-GigabitEthernet0/0/1]isis enable
[AR2-GigabitEthernet0/0/1]mpls
[AR2-GigabitEthernet0/0/1]mpls ldp
[AR2-LoopBack0]ip ad 2.2.2.2 32
[AR2-LoopBack0]isis enable
[AR3]isis
[AR3-isis-1]network-entity 49.0001.0000.0000.0003.00
[AR3-isis-1]is-level level-2
[AR3-isis-1]cost-style wide
[AR3]mpls lsr-id 3.3.3.3
[AR3]mpls
[AR3]mpls ldp
[AR3-GigabitEthernet0/0/0]ip ad 10.1.23.3 24
[AR3-GigabitEthernet0/0/0]isis enable
[AR3-GigabitEthernet0/0/0]mpls
[AR3-GigabitEthernet0/0/0]mpls ldp
[AR3-GigabitEthernet0/0/1]ip ad 10.1.34.3 24
[AR3-GigabitEthernet0/0/1]isis enable
[AR3-GigabitEthernet0/0/1]mpls
[AR3-GigabitEthernet0/0/1]mpls ldp
[AR3-GigabitEthernet0/0/2]ip ad 10.1.35.3 24
[AR3-GigabitEthernet0/0/2]isis enable
[AR3-GigabitEthernet0/0/2]mpls
[AR3-GigabitEthernet0/0/2]mpls ldp
[AR3-LoopBack0]ip ad 3.3.3.3 32
[AR3-LoopBack0]isis enable
[AR4]isis
[AR4-isis-1]network-entity 49.0001.0000.0000.0004.00
[AR4-isis-1]is-level level-2
[AR4-isis-1]cost-style wide
[AR4]mpls lsr-id 4.4.4.4
[AR4]mpls
[AR4-mpls]mpls ldp
[AR4-GigabitEthernet0/0/0]ip ad 10.1.34.4 24
[AR4-GigabitEthernet0/0/0]isis enable
[AR4-GigabitEthernet0/0/0]mpls
[AR4-GigabitEthernet0/0/0]mpls ldp
[AR4-LoopBack0]ip ad 4.4.4.4 32
[AR4-LoopBack0]isis enable
[AR5]isis
[AR5-isis-1]network-entity 49.0001.0000.0000.0005.00
[AR5-isis-1]is-level level-2
[AR5-isis-1]cost-style wide
[AR5]mpls lsr-id 5.5.5.5
[AR5]mpls
[AR5-mpls]mpls ldp
[AR5-GigabitEthernet0/0/0]ip ad 10.1.35.5 24
[AR5-GigabitEthernet0/0/0]isis enable
[AR5-GigabitEthernet0/0/0]mpls
[AR5-GigabitEthernet0/0/0]mpls ldp
[AR5-LoopBack0]ip ad 5.5.5.5 32
[AR5-LoopBack0]isis enable 分支站点配置
分支1
[AR4]ip vpn-instance A
[AR4-vpn-instance-A]route-distinguisher 100:1
[AR4-vpn-instance-A-af-ipv4]vpn-target 1:1 import-extcommunity
[AR4-vpn-instance-A-af-ipv4]vpn-target 1:2 export-extcommunity
[AR4-GigabitEthernet0/0/1]ip binding vpn-instance A
[AR4]bgp 100
[AR4-bgp]ipv4-family vpn-instance A
[AR4-bgp-A]peer 10.1.46.6 as-number 65001
[AR6-GigabitEthernet0/0/0]ip ad 10.1.46.6 24
[AR6]bgp 65001
[AR6-bgp]peer 10.1.46.4 as-number 100
分支2
[AR5]ip vpn-instance A
[AR5-vpn-instance-A]route-distinguisher 100:2
[AR5-vpn-instance-A-af-ipv4]vpn-target 1:3 import-extcommunity
[AR5-vpn-instance-A-af-ipv4]vpn-target 1:4 export-extcommunity
[AR5-GigabitEthernet0/0/1]ip binding vpn-instance A
[AR5-GigabitEthernet0/0/1]ip ad 10.1.57.5 24
[AR5]bgp 100
[AR5-bgp]ipv4-family vpn-instance A
[AR5-bgp-A]peer 10.1.57.7 as-number 65002
[AR7-GigabitEthernet0/0/0]ip ad 10.1.57.7 24
[AR7]bgp 65002
[AR7-bgp]peer 10.1.57.5 as-number 100总部站点配置
PE设备使用子接口连接站点
[AR2]ip vpn-instance A1
[AR2-vpn-instance-A1]route-distinguisher 100:100
[AR2-vpn-instance-A1-af-ipv4]vpn-target 1:2 1:4 import-extcommunity
[AR2]ip vpn-instance A2
[AR2-vpn-instance-A2]route-distinguisher 100:200
[AR2-vpn-instance-A2-af-ipv4]vpn-target 1:1 1:3 export-extcommunity
[AR2-GigabitEthernet0/0/0.1]dot1q termination vid 1
[AR2-GigabitEthernet0/0/0.1]arp broadcast enable
[AR2-GigabitEthernet0/0/0.1]ip binding vpn-instance A1
[AR2-GigabitEthernet0/0/0.1]ip ad 10.1.12.2 24
[AR2-GigabitEthernet0/0/0.2]dot1q termination vid 2
[AR2-GigabitEthernet0/0/0.2]arp broadcast enable
[AR2-GigabitEthernet0/0/0.2]ip binding vpn-instance A2
[AR2-GigabitEthernet0/0/0.2]ip ad 10.1.21.2 24
CE设备配置连接PE
[AR1-GigabitEthernet0/0/0.1]dot1q termination vid 1
[AR1-GigabitEthernet0/0/0.1]arp broadcast enable
[AR1-GigabitEthernet0/0/0.1]ip ad 10.1.12.1 24
[AR1-GigabitEthernet0/0/0.2]dot1q termination vid 2
[AR1-GigabitEthernet0/0/0.2]arp broadcast enable
[AR1-GigabitEthernet0/0/0.2]ip ad 10.1.21.1 24
总部网络协议对接
[AR1]bgp 65000
[AR1-bgp]peer 10.1.12.2 as-number 100
[AR1-bgp]peer 10.1.21.2 as-number 100
[AR2]bgp 100
[AR2-bgp]ipv4-family vpn-instance A1
[AR2-bgp-A1]peer 10.1.12.1 as-number 65000 邻居IP如果配置错误,VPN实例路由被中没有该网段,邻居无法建立
[AR2-bgp]ipv4-family vpn-instance A2
[AR2-bgp-A2]peer 10.1.21.1 as-number 65000公网建立MP-IBGP
[AR2]bgp 100
[AR2-bgp]peer 3.3.3.3 as-number 100
[AR2-bgp]peer 3.3.3.3 connect-interface LoopBack 0
[AR2-bgp]undo peer 3.3.3.3 enable
[AR2-bgp]ipv4-family vpnv4
[AR2-bgp-af-vpnv4]peer 3.3.3.3 enable
[AR4]bgp 100
[AR4-bgp]peer 3.3.3.3 as-number 100
[AR4-bgp]peer 3.3.3.3 connect-interface LoopBack 0
[AR4-bgp]undo peer 3.3.3.3 enable
[AR4-bgp]ipv4-family vpnv4
[AR4-bgp-af-vpnv4]peer 3.3.3.3 enable
[AR5]bgp 100
[AR5-bgp]peer 3.3.3.3 as-number 100
[AR5-bgp]peer 3.3.3.3 connect-interface LoopBack 0
[AR5-bgp]undo peer 3.3.3.3 enable
[AR5-bgp]ipv4-family vpnv4
[AR5-bgp-af-vpnv4]peer 3.3.3.3 enable
反射器配置
[AR3]bgp 100
[AR3-bgp]peer 2.2.2.2 as-number 100
[AR3-bgp]peer 2.2.2.2 connect-interface LoopBack 0
[AR3-bgp]peer 4.4.4.4 as-number 100
[AR3-bgp]peer 4.4.4.4 connect-interface LoopBack 0
[AR3-bgp]peer 5.5.5.5 as-number 100
[AR3-bgp]peer 5.5.5.5 connect-interface LoopBack 0
[AR3-bgp]undo peer 2.2.2.2 enable
[AR3-bgp]undo peer 4.4.4.4 enable
[AR3-bgp]undo peer 5.5.5.5 enable
[AR3-bgp-af-vpnv4]peer 2.2.2.2 enable
[AR3-bgp-af-vpnv4]peer 4.4.4.4 enable
[AR3-bgp-af-vpnv4]peer 5.5.5.5 enable
[AR3-bgp-af-vpnv4]peer 2.2.2.2 reflect-client
[AR3-bgp-af-vpnv4]peer 4.4.4.4 reflect-client
[AR3-bgp-af-vpnv4]peer 5.5.5.5 reflect-client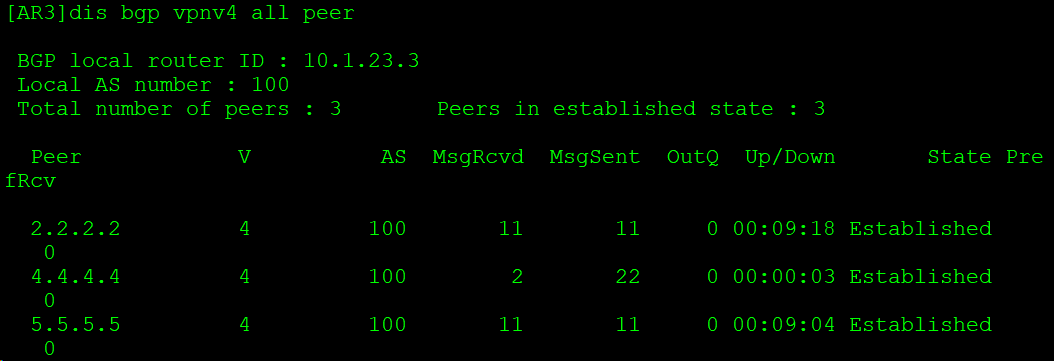 ::: warning
上述拓扑反射器可以不把AR4和AR5作为反射客户端,现网中需要考虑AR4和AR5下可能存在其他分支站点。
:::
::: warning
上述拓扑反射器可以不把AR4和AR5作为反射客户端,现网中需要考虑AR4和AR5下可能存在其他分支站点。
:::
AR7通告100.7.7.7后,AR5将VPN实例的路由转换成VPNv4路由继续传递。
[AR7-LoopBack1]ip ad 100.7.7.7 32
[AR7-bgp]network 100.7.7.7 32
[AR3-bgp]ipv4-family vpnv4
[AR3-bgp-af-vpnv4]undo policy vpn-target 反射器关闭过滤私网路由反射器AR3收到该路由:
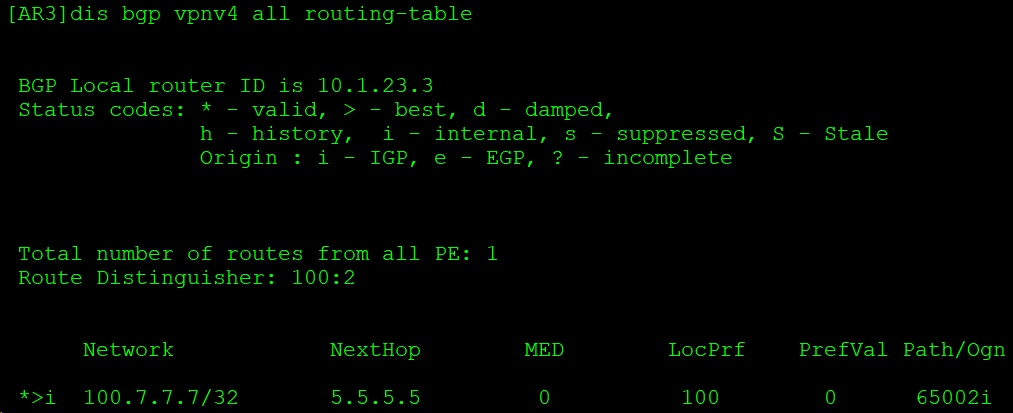 反射器AR3通告该路由:
反射器AR3通告该路由:
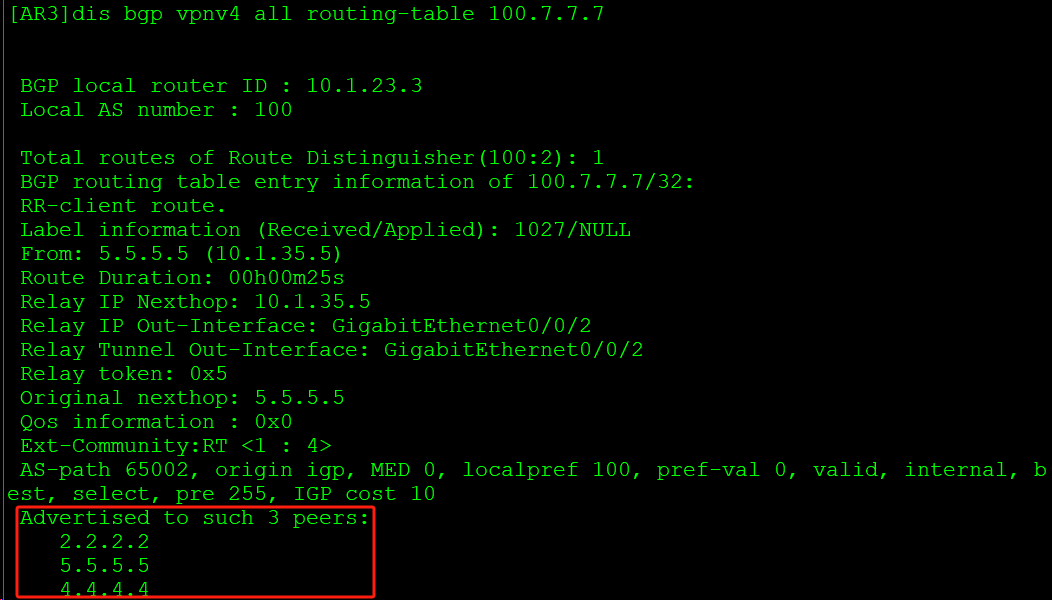 AR4的IRT没有匹配AR5的ERT,不接收AR3传来的路由:
AR4的IRT没有匹配AR5的ERT,不接收AR3传来的路由:
 总部可以正常接收分支路由(同是BGP协议不需要相互引入):
总部可以正常接收分支路由(同是BGP协议不需要相互引入):
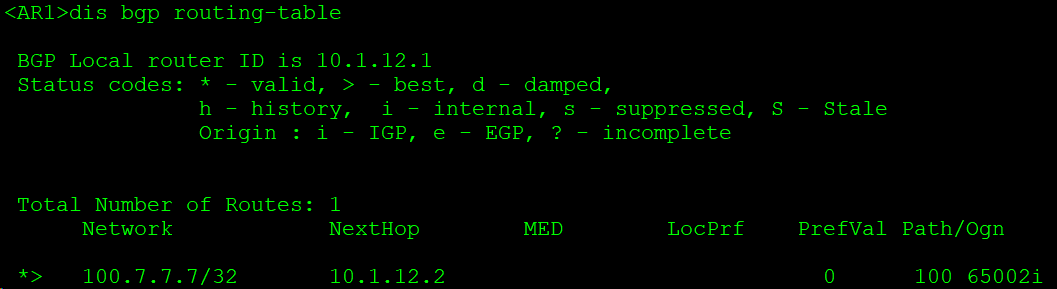 如上AR1收到100.7.7.7,下一跳是10.1.12.2,即通过VPN实例A1学习到该路由。
如上AR1收到100.7.7.7,下一跳是10.1.12.2,即通过VPN实例A1学习到该路由。
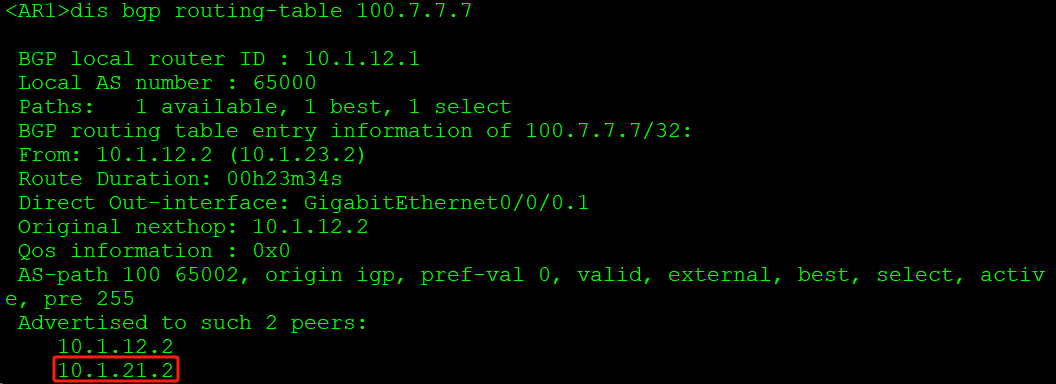 如上,AR1会将该路由通过VPN实例A2通告给AR2。
::: tip
AR2查看路由表,100.7.7.7的VPNv4路由只转换成VPN实例A1的路由:
如上,AR1会将该路由通过VPN实例A2通告给AR2。
::: tip
AR2查看路由表,100.7.7.7的VPNv4路由只转换成VPN实例A1的路由:
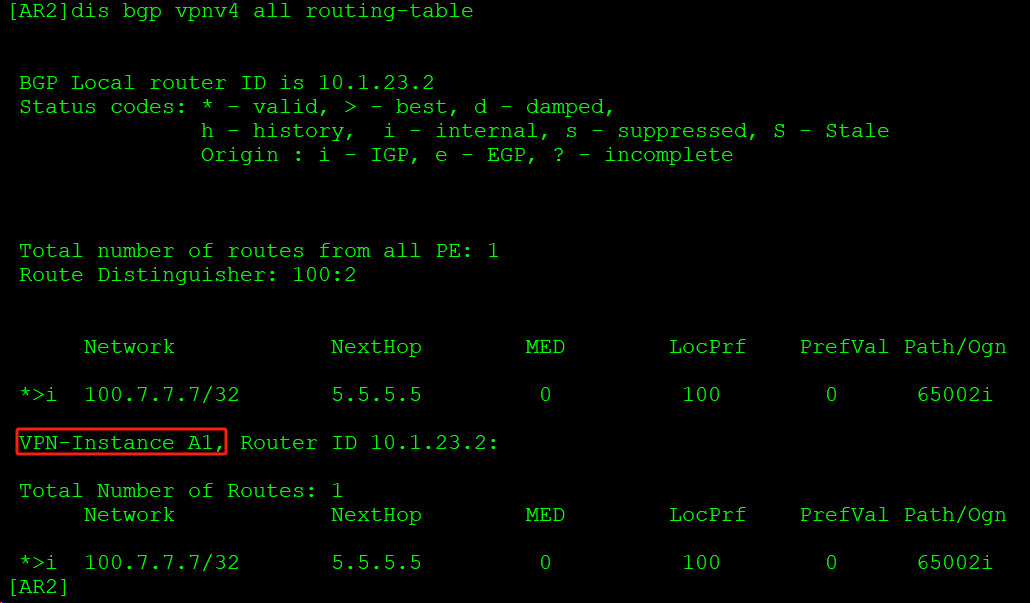 查看AR1 BGP路由表中向邻居通告该路由的明细信息:
查看AR1 BGP路由表中向邻居通告该路由的明细信息:
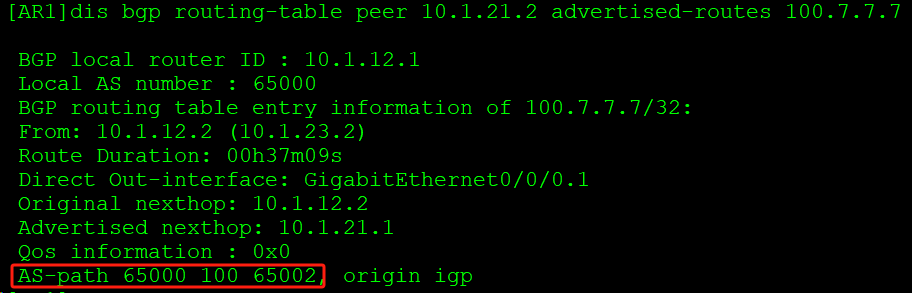 :::
::: warning
EBGP邻居拒绝接收携带AS-PATH值和自身所在AS-PATH相同的路由(防环)。
:::
:::
::: warning
EBGP邻居拒绝接收携带AS-PATH值和自身所在AS-PATH相同的路由(防环)。
:::
[AR2-bgp]ipv4-family vpn-instance A2
[AR2-bgp-A2]peer 10.1.21.1 allow-as-loop AR2从该邻居接收路由时忽略对AS-PATH的检查AR2可以接收AR1总部发来的路由(RD值100:200)转换到VPN实例A2:
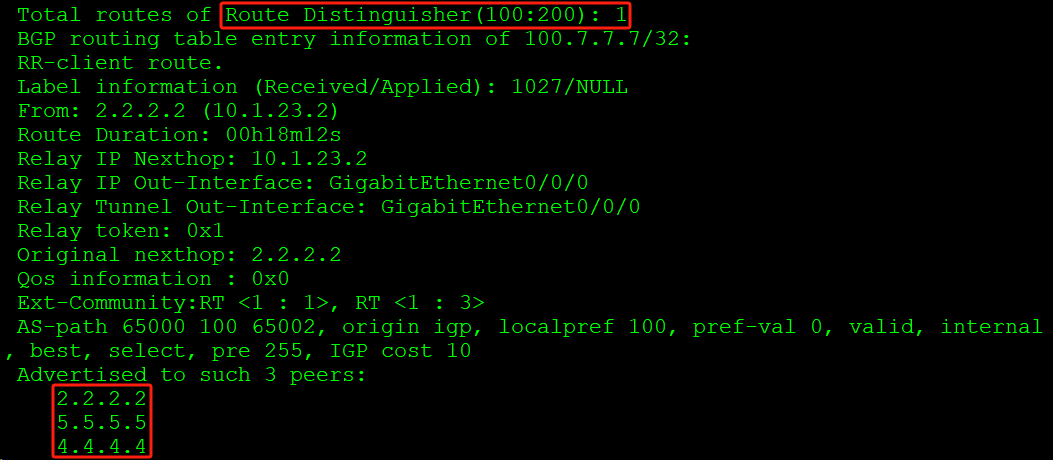
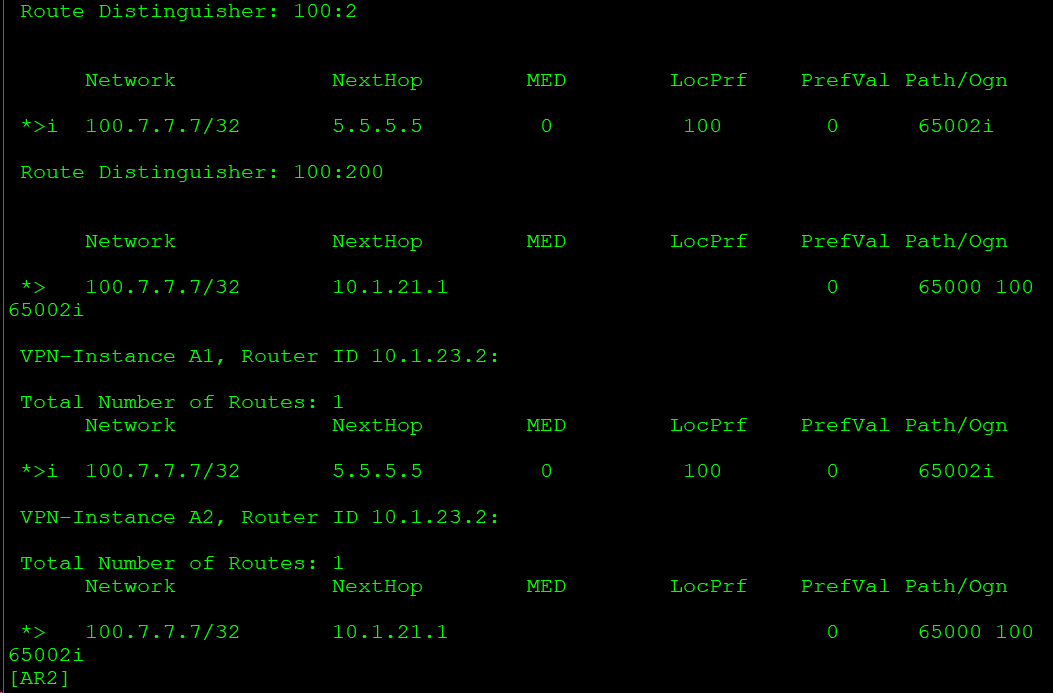 反射器AR3收到来自分支和总部的两条100.7.7.7:
反射器AR3收到来自分支和总部的两条100.7.7.7:
 AR3将两条100.7.7.7都通告出去:
AR3将两条100.7.7.7都通告出去:

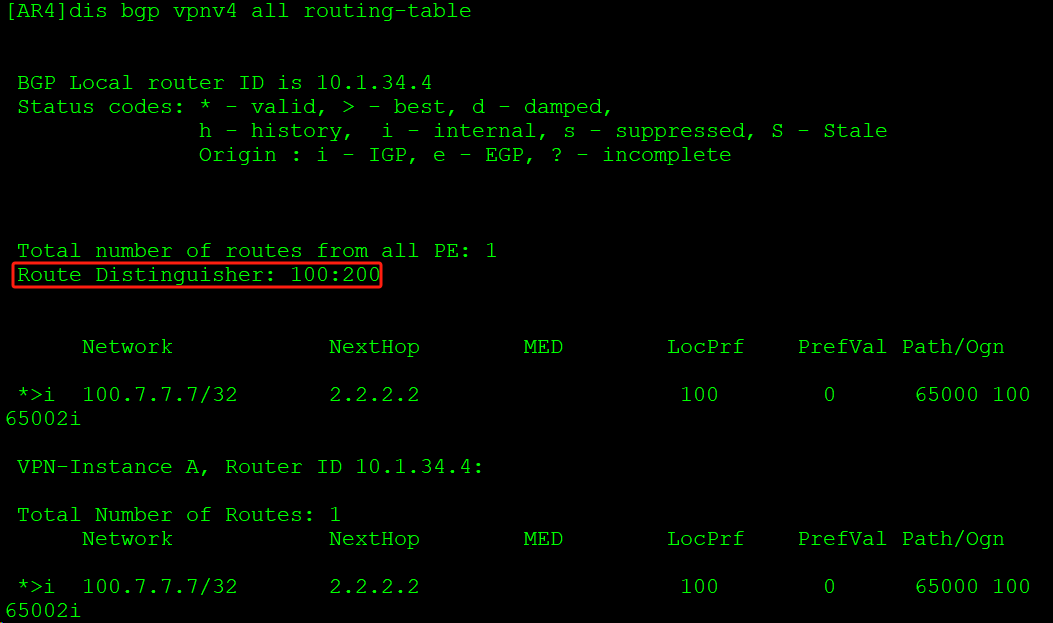
 AR4根据自身IRT值匹配发来路由的ERT,只接收总部发来的路由并转换到VPN实例中:
AR4根据自身IRT值匹配发来路由的ERT,只接收总部发来的路由并转换到VPN实例中:
 分支1收到分支2通告的路由:
分支1收到分支2通告的路由:

AR6通告100.6.6.6
[AR6-LoopBack1]ip ad 100.6.6.6 32
[AR6-bgp]network 100.6.6.6 32分支2收到分支1通告的路由:

数据包的转发过程
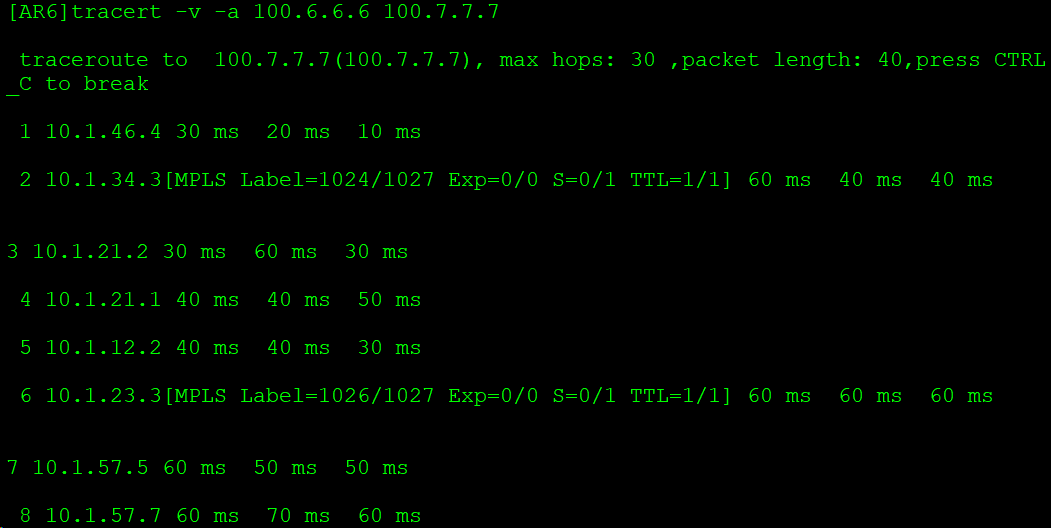
查看AR6访问AR7的标签转发路径:
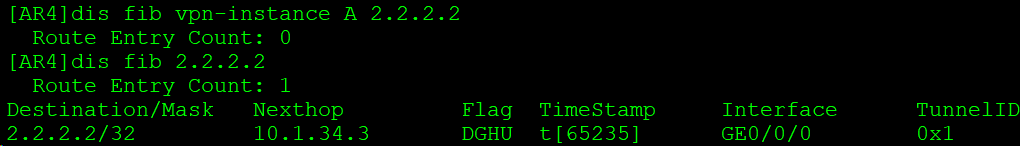
 查看AR4转发表:
查看AR4转发表:
 TunnelID不为0,表示隧道转发。查看私网路由对应标签值:
TunnelID不为0,表示隧道转发。查看私网路由对应标签值:
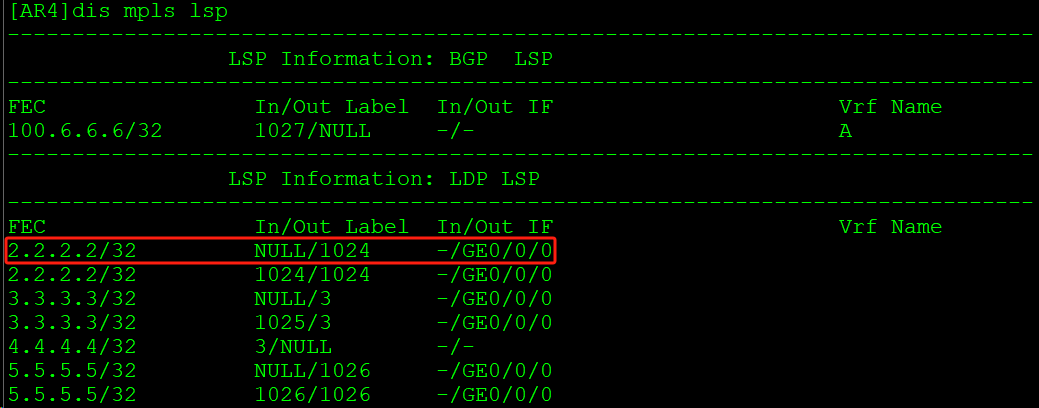
 封装私网标签1027,起源下一跳2.2.2.2。
查看AR4转发表:
封装私网标签1027,起源下一跳2.2.2.2。
查看AR4转发表:
 公网转发表中有去往下一跳的路由,TunnelID不为0,表示隧道转发。查看公网标签:
公网转发表中有去往下一跳的路由,TunnelID不为0,表示隧道转发。查看公网标签:
 封装公网标签1024,从GE0/0/0接口发给AR3:
封装公网标签1024,从GE0/0/0接口发给AR3:
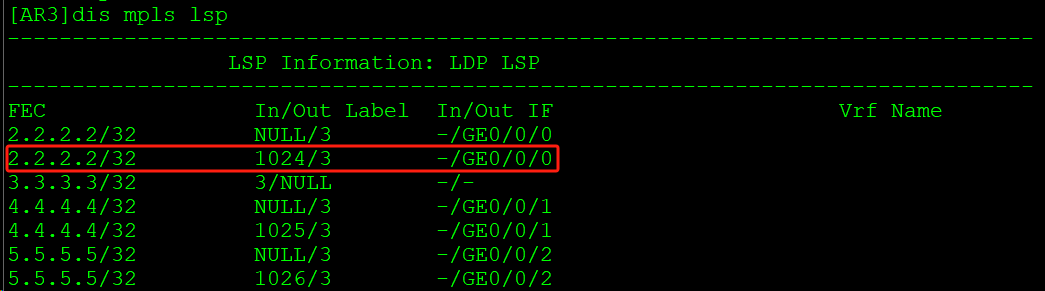 AR3将该路由的公网标签变为3,弹出公网标签,从GE0/0/0接口发给AR2:
AR3将该路由的公网标签变为3,弹出公网标签,从GE0/0/0接口发给AR2:
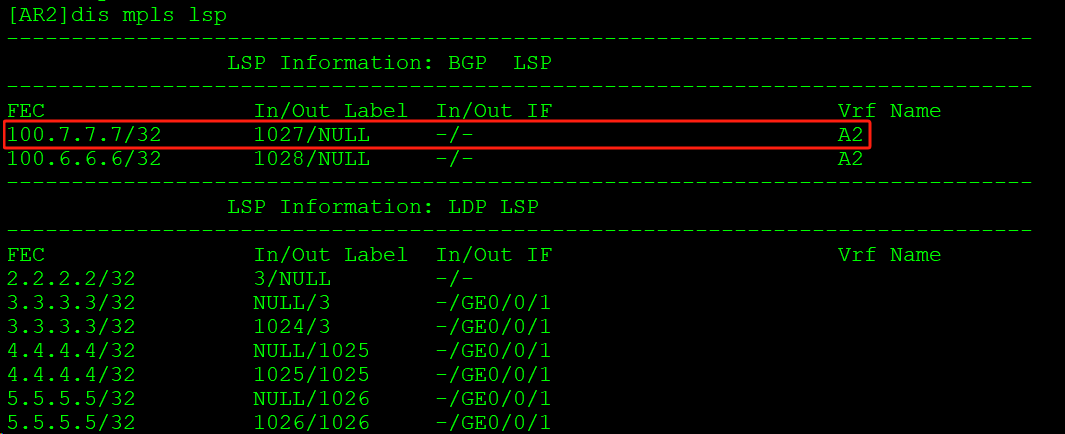 AR2 MPLS LSP表中,标签1027的路由在VPN实例A2中:
AR2 MPLS LSP表中,标签1027的路由在VPN实例A2中:
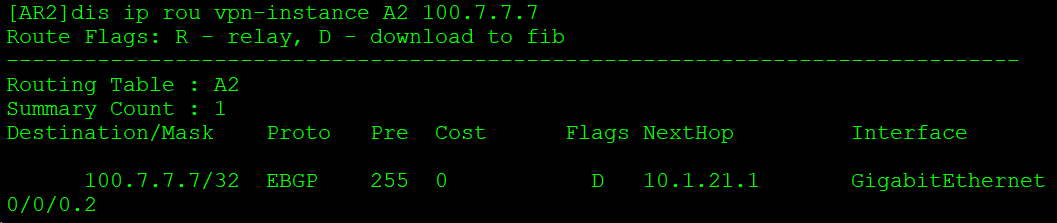 通过AR2的GE0/0/0/.2接口发出给AR1:
通过AR2的GE0/0/0/.2接口发出给AR1:
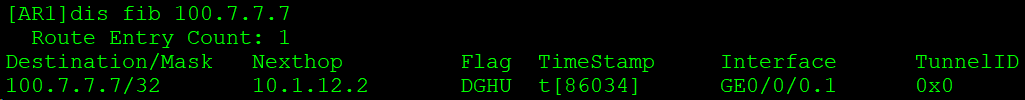 通过AR1的GE0/0/0.1接口发出给AR2,子接口0/0/.1绑定VPN实例A1:
通过AR1的GE0/0/0.1接口发出给AR2,子接口0/0/.1绑定VPN实例A1:
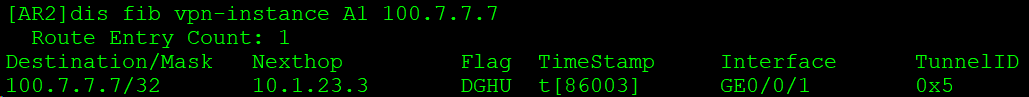 TunnelID不为0,表示隧道转发。查看私网路由对应标签值(直接查看VPN实例A1相应内容):
TunnelID不为0,表示隧道转发。查看私网路由对应标签值(直接查看VPN实例A1相应内容):
 封装私网标签1027,起源下一跳5.5.5.5。
查看AR2转发表:
封装私网标签1027,起源下一跳5.5.5.5。
查看AR2转发表:
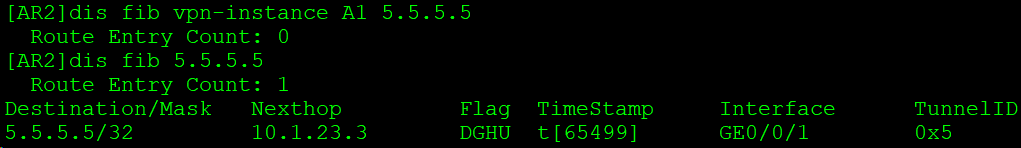 公网转发表中有去往下一跳的路由,TunnelID不为0,表示隧道转发。查看公网标签:
公网转发表中有去往下一跳的路由,TunnelID不为0,表示隧道转发。查看公网标签:
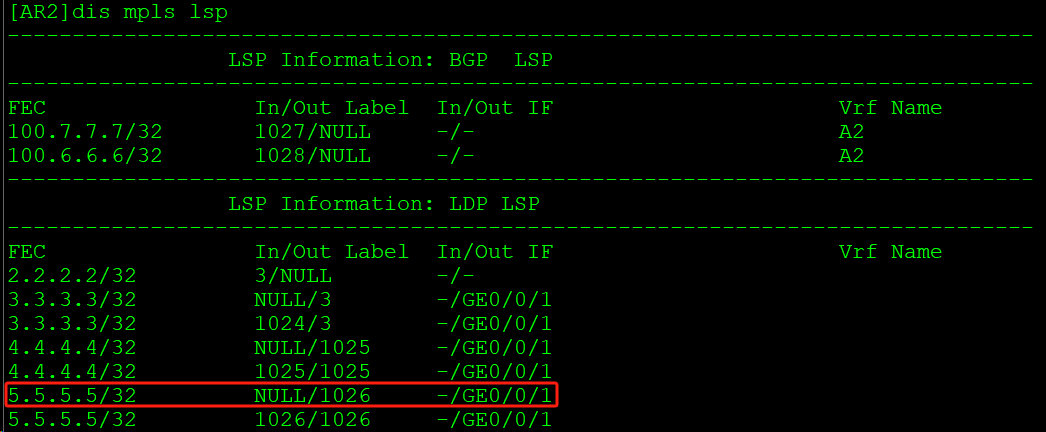 封装公网标签1026,从GE0/0/1接口发给AR3:
封装公网标签1026,从GE0/0/1接口发给AR3:
 AR3将该路由的公网标签变为3,弹出公网标签,从GE0/0/2接口发给AR5:
AR3将该路由的公网标签变为3,弹出公网标签,从GE0/0/2接口发给AR5:
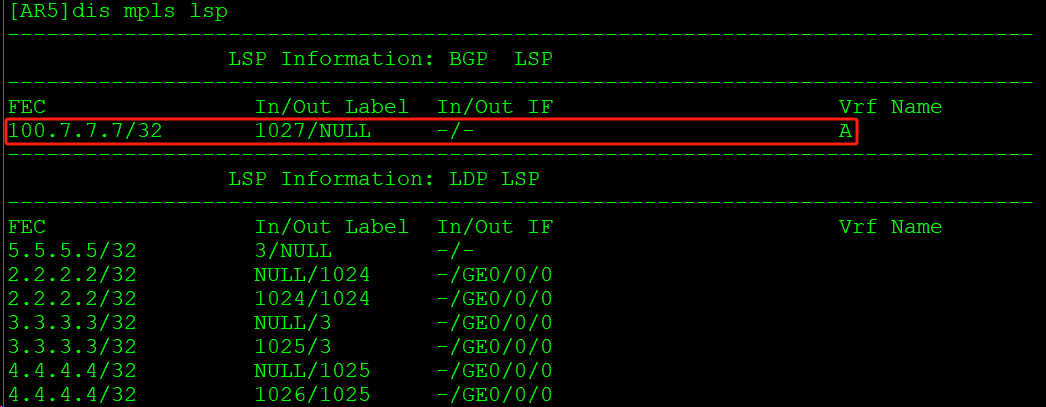 AR5 MPLS LSP表中,标签1027的路由在VPN实例A中:
AR5 MPLS LSP表中,标签1027的路由在VPN实例A中:
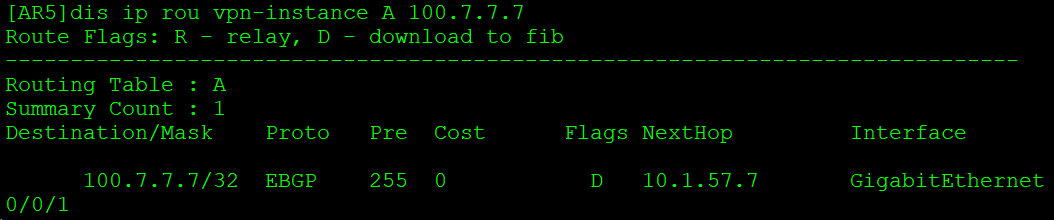 通过AR5和AR7的EBGP邻居关系,AR6的数据包达到AR7。
::: warning
数据转发方向和路由接收方向相反。
:::
通过AR5和AR7的EBGP邻居关系,AR6的数据包达到AR7。
::: warning
数据转发方向和路由接收方向相反。
:::

