@TOC

一、检查本地系统版本
检查本地环境的操作系统版本,本次实践为centos7.6版本。
[root@docker ~]# cat /etc/os-release
NAME="CentOS Linux"
VERSION="7 (Core)"
ID="centos"
ID_LIKE="rhel fedora"
VERSION_ID="7"
PRETTY_NAME="CentOS Linux 7 (Core)"
ANSI_COLOR="0;31"
CPE_NAME="cpe:/o:centos:centos:7"
HOME_URL="https://www.centos.org/"
BUG_REPORT_URL="https://bugs.centos.org/"
CENTOS_MANTISBT_PROJECT="CentOS-7"
CENTOS_MANTISBT_PROJECT_VERSION="7"
REDHAT_SUPPORT_PRODUCT="centos"
REDHAT_SUPPORT_PRODUCT_VERSION="7"二、创建redhat普通用户
1.创建redhat用户
[root@docker ~]# useradd redhat2.为redhat用户设置密码
[root@docker ~]# passwd redhat
Changing password for user redhat.
New password:
BAD PASSWORD: The password is shorter than 8 characters
Retype new password:
passwd: all authentication tokens updated successfully.3.查询创建用户相关命令的绝对路径
[root@docker ~]# which useradd
/usr/sbin/useradd
[root@docker ~]# which passwd
/usr/bin/passwd
[root@docker ~]# which userdel
/usr/sbin/userdel三、编辑/etc/sudoers文件
[root@docker ~]# vim /etc/sudoers
[root@docker ~]# grep redhat /etc/sudoers
redhat ALL=(ALL) /usr/sbin/useradd,/usr/bin/passwd,/usr/sbin/userdel
四、检查redhat用户权限
1.切换到redhat用户
[root@docker ~]# su - redhat
[redhat@docker ~]$ 2.新建huawei账号
[redhat@docker ~]$ sudo useradd huawei
We trust you have received the usual lecture from the local System
Administrator. It usually boils down to these three things:
#1) Respect the privacy of others.
#2) Think before you type.
#3) With great power comes great responsibility.
[sudo] password for redhat:
3.查看新创建用户
[redhat@docker ~]$ id huawei
uid=1002(huawei) gid=1002(huawei) groups=1002(huawei)4.为huawei账号设置密码
[redhat@docker ~]$ sudo passwd huawei
Changing password for user huawei.
New password:
BAD PASSWORD: The password is shorter than 8 characters
Retype new password:
passwd: all authentication tokens updated successfully.5.删除huawei账号
[redhat@docker ~]$ sudo userdel huawei
[redhat@docker ~]$ id huawei
id: huawei: no such user五、批量用户授权
1.设置别名
[root@docker ~]# grep -Evn '^#|^$|^##' /etc/sudoers
22:User_Alias ADMINS = zhangsan, lisi
30:Cmnd_Alias USERTEST = /usr/sbin/useradd, /usr/bin/passwd, /usr/sbin/userdel
59:Defaults !visiblepw
68:Defaults always_set_home
69:Defaults match_group_by_gid
77:Defaults always_query_group_plugin
79:Defaults env_reset
80:Defaults env_keep = "COLORS DISPLAY HOSTNAME HISTSIZE KDEDIR LS_COLORS"
81:Defaults env_keep += "MAIL PS1 PS2 QTDIR USERNAME LANG LC_ADDRESS LC_CTYPE"
82:Defaults env_keep += "LC_COLLATE LC_IDENTIFICATION LC_MEASUREMENT LC_MESSAGES"
83:Defaults env_keep += "LC_MONETARY LC_NAME LC_NUMERIC LC_PAPER LC_TELEPHONE"
84:Defaults env_keep += "LC_TIME LC_ALL LANGUAGE LINGUAS _XKB_CHARSET XAUTHORITY"
92:Defaults secure_path = /sbin:/bin:/usr/sbin:/usr/bin
104:root ALL=(ALL) ALL
105:redhat ALL=(ALL) /usr/sbin/useradd,/usr/bin/passwd,/usr/sbin/userdel
112:%wheel ALL=(ALL) ALL
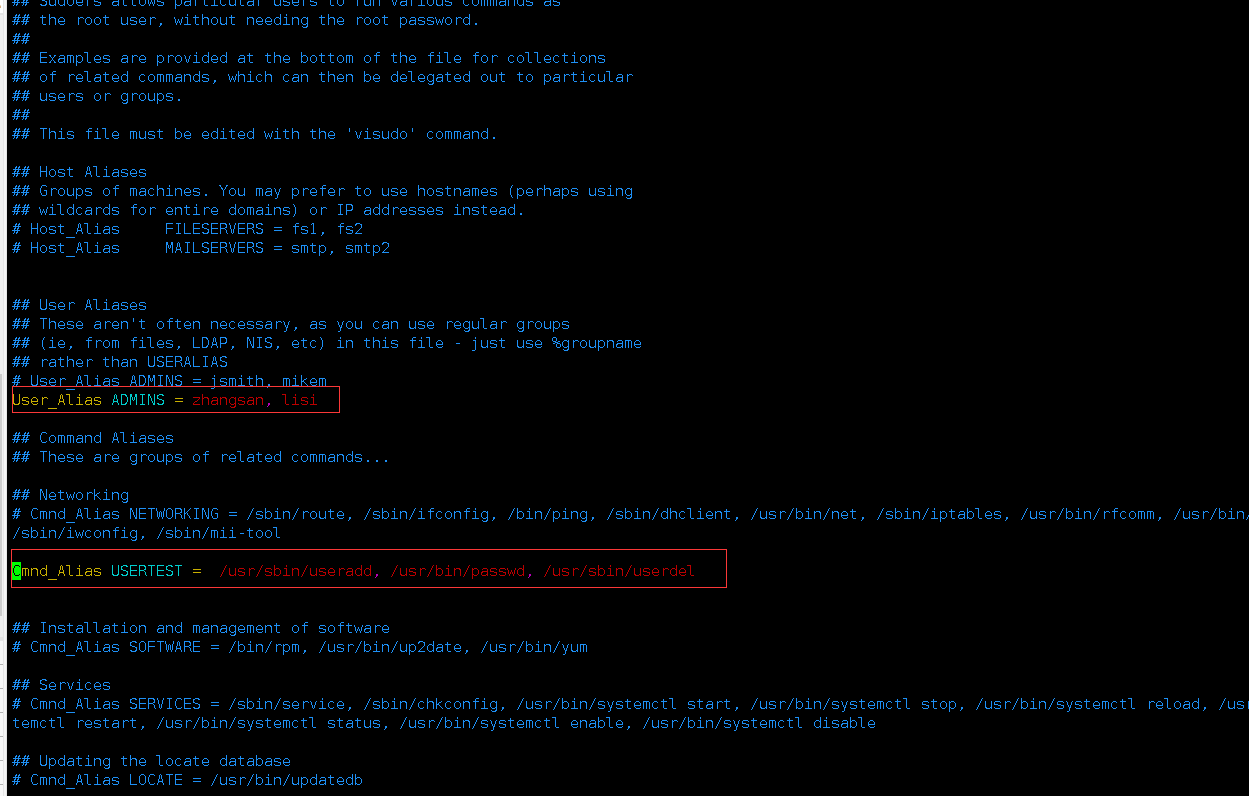
2.配置sudo授权
[root@docker ~]# grep ADMINS /etc/sudoers
# User_Alias ADMINS = jsmith, mikem
User_Alias ADMINS = zhangsan, lisi
ADMINS ALL=(ALL) USERTEST六、测试批量授权效果
1.新建用户zhangsan
[root@docker ~]# useradd zhangsan
[root@docker ~]# passwd zhangsan
Changing password for user zhangsan.
New password:
BAD PASSWORD: The password contains the user name in some form
Retype new password:
passwd: all authentication tokens updated successfully.
2.切换zhangsan用户
[root@docker ~]# su - zhangsan3.新建lisi用户并设置密码
[zhangsan@docker ~]$ sudo useradd lisi
We trust you have received the usual lecture from the local System
Administrator. It usually boils down to these three things:
#1) Respect the privacy of others.
#2) Think before you type.
#3) With great power comes great responsibility.
[sudo] password for zhangsan:
[zhangsan@docker ~]$ sudo passwd lisi
Changing password for user lisi.
New password:
BAD PASSWORD: The password is shorter than 8 characters
Retype new password:
passwd: all authentication tokens updated successfully.
4.切换lisi用户
[zhangsan@docker ~]$ su - lisi
Password:
[lisi@docker ~]$ id lisi
uid=1003(lisi) gid=1003(lisi) groups=1003(lisi)5.切换lisi用户
[zhangsan@docker ~]$ su - lisi
Password:
[lisi@docker ~]$ id lisi
uid=1003(lisi) gid=1003(lisi) groups=1003(lisi)6.测试lisi用户权限
[lisi@docker ~]$ sudo useradd user
We trust you have received the usual lecture from the local System
Administrator. It usually boils down to these three things:
#1) Respect the privacy of others.
#2) Think before you type.
#3) With great power comes great responsibility.
[sudo] password for lisi:
[lisi@docker ~]$ sudo passwd user
Changing password for user user.
New password:
BAD PASSWORD: The password is shorter than 8 characters
Retype new password:
passwd: all authentication tokens updated successfully.
[lisi@docker ~]$ id user
uid=1004(user) gid=1004(user) groups=1004(user)
[lisi@docker ~]$ sudo userdel user
[lisi@docker ~]$ id user
id: user: no such user








