SQL Server 2017的Linked Server配置触发的bug“Exception Code = c0000005 EXCEPTION_ACCESS_VIOLATION****”
现象描述:
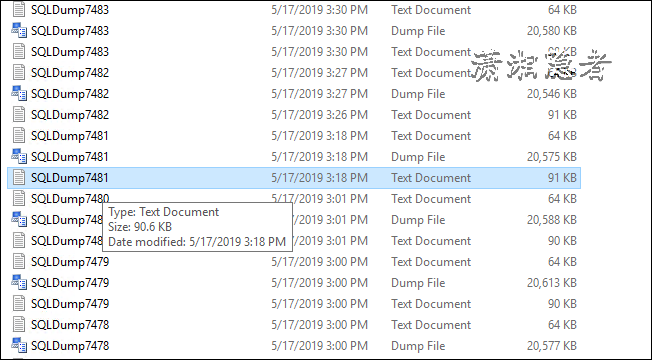
数据库版本:SQL Server 2017 (RTM-CU14) (KB4484710) - 14.0.3076.1 (X64) 出现大量的Dump File文件,如下所示:
其中一个SQLDump748.txt如下所示:
Current time is 05:00:20 05/17/19.
=====================================================================
BugCheck Dump
=====================================================================
This file is generated by Microsoft SQL Server
version 14.0.3076.1
upon detection of fatal unexpected error. Please return this file,
the query or program that produced the bugcheck, the database and
the error log, and any other pertinent information with a Service Request.
Computer type is Intel(R) Xeon(R) Gold 6148 CPU @ 2.40GHz.
Bios Version is INTEL - 6040000
PhoenixBIOS 4.0 Release 6.0
8 X64 level 8664, 2 Mhz processor (s).
Windows NT 6.2 Build 9200 CSD .
Memory
MemoryLoad = 92%
Total Physical = 131071 MB
Available Physical = 10157 MB
Total Page File = 262143 MB
Available Page File = 135435 MB
Total Virtual = 134217727 MB
Available Virtual = 133928023 MB
***Stack Dump being sent to C:\Program Files\Microsoft SQL Server\MSSQL14.MSSQLSERVER\MSSQL\LOG\SQLDump7265.txt
SqlDumpExceptionHandler: Process 59 generated fatal exception c0000005 EXCEPTION_ACCESS_VIOLATION. SQL Server is
terminating this process.
* *******************************************************************************
*
* BEGIN STACK DUMP:
* 05/17/19 05:00:20 spid 59
*
*
* Exception Address = 000001DF83DBC4AC Module(oranls11+000000000004C4AC)
* Exception Code = c0000005 EXCEPTION_ACCESS_VIOLATION
* Access Violation occurred writing address 00000000E7DF2E60
* Input Buffer 140 bytes -
* EXEC [DBO].[usp_sdAutoUploadPriceAndDeliveryDateToESCM_New]
*
*
* MODULE BASE END SIZE
* sqlservr 00007FF6C47C0000 00007FF6C483EFFF 0007f000
* ntdll 00007FFE18480000 00007FFE1864FFFF 001d0000
* KERNEL32 00007FFE16BC0000 00007FFE16C6BFFF 000ac000
* KERNELBASE 00007FFE15340000 00007FFE1555CFFF 0021d000
* SYSFER 000000006E400000 000000006E494FFF 00095000
* ADVAPI32 00007FFE16D10000 00007FFE16DB1FFF 000a2000
* msvcrt 00007FFE165D0000 00007FFE1666DFFF 0009e000
* sechost 00007FFE182D0000 00007FFE18328FFF 00059000
* RPCRT4 00007FFE16910000 00007FFE16A30FFF 00121000
* ole32 00007FFE15CE0000 00007FFE15E17FFF 00138000
* combase 00007FFE15A10000 00007FFE15CD4FFF 002c5000
* ucrtbase 00007FFE149E0000 00007FFE14AD3FFF 000f4000
* bcryptPrimitives 00007FFE14BF0000 00007FFE14C59FFF 0006a000
* GDI32 00007FFE16420000 00007FFE16453FFF 00034000
* gdi32full 00007FFE15610000 00007FFE15790FFF 00181000
* USER32 00007FFE15E80000 00007FFE15FE4FFF 00165000
* NETAPI32 00007FFE0C660000 00007FFE0C677FFF 00018000
* pdh 00007FFE11390000 00007FFE113DCFFF 0004d000
* win32u 00007FFE14970000 00007FFE1498DFFF 0001e000
* sqlmin 00007FFE02EC0000 00007FFE060B8FFF 031f9000
* sqlTsEs 00007FFE060C0000 00007FFE069EEFFF 0092f000
* sqllang 00007FFE00740000 00007FFE02EBAFFF 0277b000
* SQLOS 00007FFE06EF0000 00007FFE06EF6FFF 00007000
* sqldk 00007FFE069F0000 00007FFE06EEBFFF 004fc000
* OLEAUT32 00007FFE16500000 00007FFE165BEFFF 000bf000
* msvcp_win 00007FFE157A0000 00007FFE1583BFFF 0009c000
* opends60 00007FFE00730000 00007FFE00738FFF 00009000
* qds 00007FFE00600000 00007FFE0072BFFF 0012c000
* svl 00007FFE004E0000 00007FFE0050DFFF 0002e000
* CRYPT32 00007FFE15840000 00007FFE15A08FFF 001c9000
* MSASN1 00007FFE14910000 00007FFE1491FFFF 00010000
* WS2_32 00007FFE18350000 00007FFE183B9FFF 0006a000
* MSVCP120 00007FFE0BDF0000 00007FFE0BE95FFF 000a6000
* MSVCR120 00007FFE0D6B0000 00007FFE0D79EFFF 000ef000
* WINMM 00007FFE12CF0000 00007FFE12D12FFF 00023000
* Secur32 00007FFE11250000 00007FFE1125BFFF 0000c000
* WINHTTP 00007FFE11280000 00007FFE1134BFFF 000cc000
* ODBC32 00007FFE00430000 00007FFE004DEFFF 000af000
* secforwarder 00007FFE00510000 00007FFE00519FFF 0000a000
* WINMMBASE 00007FFE12C90000 00007FFE12CBAFFF 0002b000
* cfgmgr32 00007FFE14990000 00007FFE149D1FFF 00042000
* bcrypt 00007FFE14820000 00007FFE1484AFFF 0002b000
* ncrypt 00007FFE14430000 00007FFE14455FFF 00026000
* NTASN1 00007FFE143F0000 00007FFE1442AFFF 0003b000
* SSPICLI 00007FFE14550000 00007FFE1457BFFF 0002c000
* NETUTILS 00007FFE13F70000 00007FFE13F7CFFF 0000d000
* DPAPI 00007FFE13B20000 00007FFE13B29FFF 0000a000
* SAMCLI 00007FFE11F50000 00007FFE11F68FFF 00019000
* WINTRUST 00007FFE14B90000 00007FFE14BE4FFF 00055000
* USERENV 00007FFE14030000 00007FFE1404EFFF 0001f000
* AUTHZ 00007FFE13BC0000 00007FFE13C09FFF 0004a000
* profapi 00007FFE148E0000 00007FFE148F3FFF 00014000
* XmlLite 00007FFE0C8F0000 00007FFE0C925FFF 00036000
* dhcpcsvc 00007FFE11260000 00007FFE11279FFF 0001a000
* WININET 00007FFE07D40000 00007FFE08121FFF 003e2000
* NSI 00007FFE165C0000 00007FFE165C7FFF 00008000
* LOGONCLI 00007FFE12780000 00007FFE127BDFFF 0003e000
* psapi 00007FFE18340000 00007FFE18347FFF 00008000
* kernel.appcore 00007FFE14900000 00007FFE1490EFFF 0000f000
* instapi140 00007FFDFD330000 00007FFDFD342FFF 00013000
* CRYPTSP 00007FFE14350000 00007FFE14366FFF 00017000
* rsaenh 00007FFE13DC0000 00007FFE13DF2FFF 00033000
* CRYPTBASE 00007FFE14370000 00007FFE1437AFFF 0000b000
* imagehlp 00007FFE16A40000 00007FFE16A5BFFF 0001c000
* gpapi 00007FFE138D0000 00007FFE138F2FFF 00023000
* wkscli 00007FFE10DE0000 00007FFE10DF5FFF 00016000
* cscapi 00007FFDFD350000 00007FFDFD361FFF 00012000
* sqlevn70 000001DFEAF90000 000001DFEB29EFFF 0030f000
* CLUSAPI 00007FFE09EE0000 00007FFE09F98FFF 000b9000
* DNSAPI 00007FFE13F80000 00007FFE14020FFF 000a1000
* IPHLPAPI 00007FFE13F30000 00007FFE13F67FFF 00038000
* RESUTILS 00007FFE0A1B0000 00007FFE0A210FFF 00061000
* VERSION 00007FFE0C490000 00007FFE0C499FFF 0000a000
* hkruntime 00007FFDFD490000 00007FFDFD760FFF 002d1000
* hkcompile 00007FFDFC470000 00007FFDFC5D1FFF 00162000
* SHLWAPI 00007FFE183C0000 00007FFE18411FFF 00052000
* hkengine 00007FFDFBC30000 00007FFDFC33AFFF 0070b000
* dbghelp 000000006D570000 000000006D705FFF 00196000
* ncryptprov 00007FFE0D9D0000 00007FFE0DA23FFF 00054000
* msv1_0 00007FFE14140000 00007FFE141A6FFF 00067000
* NtlmShared 00007FFE14130000 00007FFE1413BFFF 0000c000
* cryptdll 00007FFE14210000 00007FFE14224FFF 00015000
* kerberos 00007FFE14260000 00007FFE1434FFFF 000f0000
* schannel 00007FFE13D00000 00007FFE13D77FFF 00078000
* SECURITY 000002073E580000 000002073E582FFF 00003000
* MSCOREE 00007FFE07B20000 00007FFE07B85FFF 00066000
* mscoreei 00007FFE07A80000 00007FFE07B1BFFF 0009c000
* SqlServerSpatial140 00007FFDFB8F0000 00007FFDFB9A1FFF 000b2000
* clbcatq 00007FFE16C70000 00007FFE16D0EFFF 0009f000
* msxml3 00007FFDFB640000 00007FFDFB86BFFF 0022c000
* sqlncli11 00007FFDFB2E0000 00007FFDFB632FFF 00353000
* COMDLG32 00007FFE16810000 00007FFE16909FFF 000fa000
* shcore 00007FFE14AE0000 00007FFE14B88FFF 000a9000
* SHELL32 00007FFE16DC0000 00007FFE182C4FFF 01505000
* windows.storage 00007FFE14C60000 00007FFE15338FFF 006d9000
* powrprof 00007FFE14920000 00007FFE1496BFFF 0004c000
* MSVCR100 000000006D490000 000000006D561FFF 000d2000
* COMCTL32 00007FFE07C90000 00007FFE07D3BFFF 000ac000
* imm32 00007FFE16460000 00007FFE1648DFFF 0002e000
* SQLNCLIR11 000002073E710000 000002073E747FFF 00038000
* netbios 00007FFDFC340000 00007FFDFC34BFFF 0000c000
* sqlnclirda11 000000006D130000 000000006D488FFF 00359000
* ualapi 00007FFDFB2C0000 00007FFDFB2D9FFF 0001a000
* ESENT 00007FFE094E0000 00007FFE097D1FFF 002f2000
* ntmarta 00007FFE13610000 00007FFE13641FFF 00032000
* SQLNCLIRDAR11 000002073E810000 000002073E847FFF 00038000
* clr 00007FFE06F00000 00007FFE078ECFFF 009ed000
* MSVCR120_CLR0400 00007FFE00270000 00007FFE00366FFF 000f7000
* mscorlib.ni 00007FFDFEAB0000 00007FFE00040FFF 01591000
* SqlAccess 00007FFDFB240000 00007FFDFB2B4FFF 00075000
* clrjit 00007FFDFD770000 00007FFDFD89AFFF 0012b000
* BatchParser 00007FFDFAC50000 00007FFDFAC7BFFF 0002c000
* SRVCLI 00007FFE09E70000 00007FFE09E95FFF 00026000
* ftimport 0000000060000000 0000000060024FFF 00025000
* MSFTE 0000000049980000 0000000049D2DFFF 003ae000
* mskeyprotect 00007FFDFB870000 00007FFDFB884FFF 00015000
* mswsock 00007FFE141B0000 00007FFE1420BFFF 0005c000
* ntdsapi 00007FFE0A350000 00007FFE0A378FFF 00029000
* DSPARSE 00007FFE0EE40000 00007FFE0EE4CFFF 0000d000
* rasadhlp 00007FFE104B0000 00007FFE104B9FFF 0000a000
* fwpuclnt 00007FFE11780000 00007FFE117E9FFF 0006a000
* ncryptsslp 00007FFDFB8C0000 00007FFDFB8E0FFF 00021000
* xpsqlbot 00007FFE0B930000 00007FFE0B937FFF 00008000
* xpstar 00007FFE0B0A0000 00007FFE0B10DFFF 0006e000
* SQLSCM 00007FFDFB090000 00007FFDFB0A2FFF 00013000
* xpstar 0000020923680000 000002092368CFFF 0000d000
* cryptnet 00007FFDF7D10000 00007FFDF7D3EFFF 0002f000
* xplog70 00007FFDFD3A0000 00007FFDFD3B3FFF 00014000
* xplog70 000001DF80010000 000001DF80013FFF 00004000
* Sort00060101 00007FFDF1030000 00007FFDF1042FFF 00013000
* mlang 00007FFDF0D20000 00007FFDF0D5EFFF 0003f000
* System.Data 00007FFDF8E30000 00007FFDF9195FFF 00366000
* wldp 00007FFE13B00000 00007FFE13B17FFF 00018000
* odsole70 00007FFE08440000 00007FFE08457FFF 00018000
* scrrun 00007FFDFC3D0000 00007FFDFC401FFF 00032000
* sxs 00007FFE14720000 00007FFE147B7FFF 00098000
* oledb32 00007FFDEC730000 00007FFDEC81CFFF 000ed000
* MSDART 00007FFE07A50000 00007FFE07A75FFF 00026000
* Comctl32 00007FFDFB9B0000 00007FFDFBC29FFF 0027a000
* msadce 00007FFDEF670000 00007FFDEF70BFFF 0009c000
* msadcer 000001DF82CD0000 000001DF82CD2FFF 00003000
* sqloledb 00007FFDE9300000 00007FFDE93D6FFF 000d7000
* MSDATL3 00007FFDFAC90000 00007FFDFACB1FFF 00022000
* OraOLEDB11 0000000010000000 000000001008EFFF 0008f000
* OraOLEDBgmr11 0000000044100000 0000000044126FFF 00027000
* OraOLEDBrst11 0000000044400000 0000000044434FFF 00035000
* OraOLEDButl11 0000000044700000 0000000044708FFF 00009000
* OCI 0000000180000000 00000001800AAFFF 000ab000
* MSVCR80 000000006DE00000 000000006DEC8FFF 000c9000
* OraClient11 000001DF838D0000 000001DF83D6DFFF 0049e000
* oracore11 000001DF82DE0000 000001DF82F3FFFF 00160000
* oranls11 000001DF83D70000 000001DF83E6EFFF 000ff000
* oraunls11 000001DF82DA0000 000001DF82DBFFFF 00020000
* oracommon11 000001DF83E70000 000001DF84126FFF 002b7000
* orageneric11 000001DF84130000 000001DF85030FFF 00f01000
* oran11 000001DF85040000 000001DF85493FFF 00454000
* orancrypt11 000001DF854A0000 000001DF854C3FFF 00024000
* oraldapclnt11 000001DF854D0000 000001DF856C1FFF 001f2000
* oranl11 000001DF856E0000 000001DF8574EFFF 0006f000
* oranro11 000001DF85760000 000001DF857BAFFF 0005b000
* orapls11 000001DF857D0000 000001DF85CF0FFF 00521000
* orasql11 000001DF85D10000 000001DF85D6DFFF 0005e000
* orauts 000001DF85D80000 000001DF85D86FFF 00007000
* orasnls11 000001DF85DA0000 000001DF85DDCFFF 0003d000
* oraxml11 000001DF85DF0000 000001DF862CEFFF 004df000
* oracell11 000001DF862E0000 000001DF8632AFFF 0004b000
* orannzsbb11 000001DF86340000 000001DF864C3FFF 00184000
* orahasgen11 000001DF864E0000 000001DF867B5FFF 002d6000
* oraocr11 000001DF867D0000 000001DF86897FFF 000c8000
* orazt11 000001DF868B0000 000001DF86A9FFFF 001f0000
* oranldap11 000001DF86AB0000 000001DF86AFAFFF 0004b000
* oranhost11 000001DF86B10000 000001DF86B19FFF 0000a000
* orancds11 000001DF86B30000 000001DF86B36FFF 00007000
* orantns11 000001DF86B50000 000001DF86B60FFF 00011000
* oraztkg11 000001DF86B80000 000001DF86C32FFF 000b3000
* WSOCK32 00007FFE09100000 00007FFE09108FFF 00009000
* orantcp11 000001DF86C50000 000001DF86C84FFF 00035000
* oraslax11 000001DF86CA0000 000001DF86CAEFFF 0000f000
* oravsn11 000001DF86CC0000 000001DF86CC6FFF 00007000
* oraplp11 000001DF86CE0000 000001DF870D4FFF 003f5000
* MSVCP80 000000006DF80000 000000006E088FFF 00109000
* oraocrutl11 000001DF870F0000 000001DF87100FFF 00011000
* oraocrb11 000001DF87120000 000001DF87213FFF 000f4000
* OraPlc11 000001DF87230000 000001DF8724FFFF 00020000
* OraOLEDB11us 0000000044300000 0000000044305FFF 00006000
* OraOLEDBpus11 0000000044200000 0000000044207FFF 00008000
* msdaps 00007FFE0B1F0000 00007FFE0B250FFF 00061000
* comsvcs 00007FFE0B280000 00007FFE0B41BFFF 0019c000
* napinsp 00007FFE0DA30000 00007FFE0DA45FFF 00016000
* winrnr 00007FFE0DCA0000 00007FFE0DCADFFF 0000e000
* NLAapi 00007FFE11620000 00007FFE11637FFF 00018000
* apphelp 00007FFE12C10000 00007FFE12C89FFF 0007a000
* DSROLE 00007FFE122C0000 00007FFE122C9FFF 0000a000
* rasapi32 00007FFDEF7C0000 00007FFDEF877FFF 000b8000
* rasman 00007FFDFB1A0000 00007FFDFB1BFFFF 00020000
* rtutils 00007FFE0E2B0000 00007FFE0E2C3FFF 00014000
* dhcpcsvc6 00007FFE10F10000 00007FFE10F25FFF 00016000
* System.ni 00007FFDFDA50000 00007FFDFE690FFF 00c41000
* System.Transactions 00007FFE0D7B0000 00007FFE0D7FEFFF 0004f000
* System.Security.ni 00007FFDFE8B0000 00007FFDFE9A0FFF 000f1000
* System.Xml.ni 00007FFDF9AE0000 00007FFDFA36BFFF 0088c000
* System.Core.ni 00007FFDFC8A0000 00007FFDFD2EFFFF 00a50000
* System.Configuration.ni 00007FFDF8D00000 00007FFDF8E2AFFF 0012b000
* COMRES 000001DF88040000 000001DF8817DFFF 0013e000
* XOLEHLP 00007FFDF1540000 00007FFDF1556FFF 00017000
* MSDTCPRX 00007FFDFAB60000 00007FFDFAC41FFF 000e2000
* MTXCLU 00007FFDFAAF0000 00007FFDFAB58FFF 00069000
* ktmw32 00007FFE0B090000 00007FFE0B09AFFF 0000b000
* ondemandconnroutehelper 00007FFE10360000 00007FFE10374FFF 00015000
* clrcompression 00007FFE0DC50000 00007FFE0DC73FFF 00024000
* SAMLIB 00007FFE0D100000 00007FFE0D122FFF 00023000
* xprepl 00007FFE0B1D0000 00007FFE0B1E9FFF 0001a000
* dbghelp 000000006CE90000 000000006D025FFF 00196000
*
* P1Home: 0000000000000000:
* P2Home: 0000000000000000:
* P3Home: 000000000000000C:
* P4Home: 0000000000000000:
* P5Home: 0000000000000000:
* P6Home: 0000000000000000:
* ContextFlags: 000000000010005F:
* MxCsr: 0000000000001F80:
* SegCs: 0000000000000033:
* SegDs: 000000000000002B:
* SegEs: 000000000000002B:
* SegFs: 0000000000000053:
* SegGs: 000000000000002B:
* SegSs: 000000000000002B:
* EFlags: 0000000000010246:
* Rax: 000000000000000C:
* Rcx: 0000000000000031:
* Rdx: 0000000000000031:
* Rbx: 000000000000000C:
* Rsp: 00000064EC3F80F0: 0000000000000000 000001DFB38C02A0 0000000000000020 000001DFEA290D50 00000226
00000028 000001DF8474C4F0
* Rbp: 00000000E7DF2E60:
* Rsi: 000001DF8726D7E0: 0B20010003000000 000026D900003085 0000000200000000 0000000000015A00 00000000
00000000 0000000000000000
* Rdi: 000001DF88630008: 000001DF88630018 000001DF83E5F120 000001DF87265840 0000000000000000 00000000
00000000 000000000000001C
* R8: 00000000E7DF2E60:
* R9: 00000225BF9B38C8: 2073776F72203631 000000006C696166 0000000000000000 0000000000000000 00000000
00000000 0000000000000000
* R10: 00000000000000B2:
* R11: 0000000000000001:
* R12: 00000000E7DF2E60:
* R13: 00000225BF9B38C8: 2073776F72203631 000000006C696166 0000000000000000 0000000000000000 00000000
00000000 0000000000000000
* R14: 000000000000000C:
* R15: 000000000000000C:
* Rip: 000001DF83DBC4AC: 01C58349004D8966 35740000FFFDF981 75FFC08302C58348 2B4D1E77FE3B45DA E82B4928
6F894CE9 C48348E889FDD148
* *******************************************************************************
* -------------------------------------------------------------------------------
* Short Stack Dump
000001DF83DBC4AC Module(oranls11+000000000004C4AC)
0000000180064570 Module(OCI+0000000000064570)
000000004440CC35 Module(OraOLEDBrst11+000000000000CC35)
000000004442647B Module(OraOLEDBrst11+000000000002647B)
000000001002F10A Module(OraOLEDB11+000000000002F10A)
00000000100325CA Module(OraOLEDB11+00000000000325CA)
0000000010035C78 Module(OraOLEDB11+0000000000035C78)
00007FFDEC7A9262 Module(oledb32+0000000000079262)
00007FFDEC7AA945 Module(oledb32+000000000007A945)
00007FFE016B51DD Module(sqllang+0000000000F751DD)
00007FFE0169D838 Module(sqllang+0000000000F5D838)
00007FFE016114BE Module(sqllang+0000000000ED14BE)
00007FFE01395A94 Module(sqllang+0000000000C55A94)
00007FFE013984C8 Module(sqllang+0000000000C584C8)
00007FFE01381DDC Module(sqllang+0000000000C41DDC)
00007FFE0137CE68 Module(sqllang+0000000000C3CE68)
00007FFE00754E70 Module(sqllang+0000000000014E70)
00007FFE00755823 Module(sqllang+0000000000015823)
00007FFE00755F24 Module(sqllang+0000000000015F24)
00007FFE013802F3 Module(sqllang+0000000000C402F3)
00007FFE0137FC90 Module(sqllang+0000000000C3FC90)
00007FFE0137CA68 Module(sqllang+0000000000C3CA68)
00007FFE00754E70 Module(sqllang+0000000000014E70)
00007FFE00755823 Module(sqllang+0000000000015823)
00007FFE00755F24 Module(sqllang+0000000000015F24)
00007FFE013802F3 Module(sqllang+0000000000C402F3)
00007FFE0137FC90 Module(sqllang+0000000000C3FC90)
00007FFE0137CA68 Module(sqllang+0000000000C3CA68)
00007FFE00754E70 Module(sqllang+0000000000014E70)
00007FFE00755823 Module(sqllang+0000000000015823)
00007FFE00755F24 Module(sqllang+0000000000015F24)
00007FFE0075CB7D Module(sqllang+000000000001CB7D)
00007FFE00753B12 Module(sqllang+0000000000013B12)
00007FFE00753903 Module(sqllang+0000000000013903)
00007FFE069F4DAD Module(sqldk+0000000000004DAD)
00007FFE069F52E8 Module(sqldk+00000000000052E8)
00007FFE069F4F5D Module(sqldk+0000000000004F5D)
00007FFE06A15818 Module(sqldk+0000000000025818)
00007FFE06A15910 Module(sqldk+0000000000025910)
00007FFE06A15087 Module(sqldk+0000000000025087)
00007FFE06A155D9 Module(sqldk+00000000000255D9)
00007FFE16BC84D4 Module(KERNEL32+00000000000084D4)
00007FFE184EE851 Module(ntdll+000000000006E851)
CSession @0x000001EE926287B0
----------------------------
m_sessionId = 59 m_cRef = 18 m_rgcRefType[0] = 1
m_rgcRefType[1] = 1 m_rgcRefType[2] = 15 m_rgcRefType[3] = 1
m_rgcRefType[4] = 0 m_rgcRefType[5] = 0 m_pmo = 0x000001EE92628040
m_pstackBhfPool = 0x000001EC206375F0 m_dwLoginFlags = 0x100083e0 m_fBackground = 0
m_eConnResetOption = 0 m_fUserProc = 1 m_fConnReset = 0
m_fIsConnReset = 0 m_fInLogin = 0 m_fAuditLoginSent = 1
m_fAuditLoginFailedSent = 0 m_fReplRelease = 0 m_fKill = 0
m_ulLoginStamp = 72716430 m_eclClient = 7 m_protType = 6
CUEnvTransient @0x000001EE92628C90
----------------------------------
m_ululRowcount = 0 m_cidLastOpen = 0 m_lFetchStat = 0
m_lRetStat = 0 m_lLastError = 0 m_lPrevError = 0
m_cNestLevel = 0 m_lHoldRand1 = 0 m_lHoldRand2 = 0
m_cbContextInfo = 0 m_rgbContextInfo = 000001EE92628E8C
CDbAndSetOpts @0x000001EE92628CB0
---------------------------------
m_fHasDbRef = 0 m_fDateFirstSet = 0 m_fDateFormatSet = 0
m_lUserOpt1 = 0x14016000 m_lUserOpt2 = 0x0 m_lUserOpt1SetMask = 0xffffe7f7
m_idtInsert.objid = 0 m_idtInsert.state = 0 m_idtInsert.dbid = 0
m_llRowcnt = 0 m_lStatList = 0 m_lTextSize = 1024
m_lOffsets = 0x0 m_ulLockTimeout = 4294967295 m_ulQueryGov = 0
m_eDtFmt = 1 m_eDayDateFirst = 7 m_eDdLckPri = 0
m_eIsoLvl = 2 m_eFipsFlag = 0x0 m_sLangId = 0
m_pV7LoginRec
---------------------
0000000000000000: a4010000 04000074 00100000 00000007 50300000 ¤......t........P0..
0000000000000014: 00000000 e0830010 20feffff 09040000 5e000800 ....à.. þÿÿ ...^...
0000000000000028: 00000000 00000000 6e004900 00010700 0e010400 ........n.I.........
000000000000003C: 12010400 1a010000 1a010600 005056b4 c19c2601 .............PV´Á&.
0000000000000050: 78002601 00000000 00000000 0000 x.&...........
CPhysicalConnection @0x000001EE92628400
---------------------------------------
m_pPhyConn->m_pmo = 0x000001EE92628040
m_pPhyConn->m_pNetConn = 0x000001EE92629070
m_pPhyConn->m_pConnList = 0x000001EE92628780
m_pPhyConn->m_pSess = 0x000001EE92628808 m_pPhyConn->m_fTracked = -1
m_pPhyConn->m_cbPacketsize = 4096 m_pPhyConn->m_fMars = 0 m_pPhyConn->m_fKill = 0
CBatch @0x000001EE92629CB0
--------------------------
m_pSess = 0x000001EE926287B0 m_pConn = 0x000001EE926296B0 m_cRef = 3
m_rgcRefType[0] = 1 m_rgcRefType[1] = 1 m_rgcRefType[2] = 1
m_rgcRefType[3] = 0 m_rgcRefType[4] = 0 m_pTask = 0x000001EBB55C84E8
EXCEPT (null) @0x00000064EC3F4EF8
---------------------------------
exc_number = 0 exc_severity = 0 exc_func = sqldk.dll+0x000000000005D430
Task @0x000001EBB55C84E8
------------------------
CPU Ticks used (ms) = 20055 Task State = 2
WAITINFO_INTERNAL: WaitResource = 0x0000000000000000 WAITINFO_INTERNAL: WaitType = 0x0
WAITINFO_INTERNAL: WaitSpinlock = 0x0000000000000000
WAITINFO_EXTERNAL: WaitResource = 0x0000000000000000 WAITINFO_EXTERNAL: WaitType = 0x400070
WAITINFO_EXTERNAL: WaitSpinlock = 0x0000000000000000
WAITINFO_EXTERNAL: WaitResource = 0x0000000000000000
WAITINFO_EXTERNAL: WaitType = 0x200001D7
WAITINFO_EXTERNAL: WaitSpinlock = 0x0000000000000000
WAITINFO_EXTERNAL: WaitResource = 0x0000000000000000 WAITINFO_EXTERNAL: WaitType = 0x4000DA
WAITINFO_EXTERNAL: WaitSpinlock = 0x0000000000000000 SchedulerId = 0x3
ThreadId = 0x3620 m_state = 0 m_eAbortSev = 0
EC @0x000001EC20637720
----------------------
spid = 0 ecid = 0 ec_stat = 0x0
ec_stat2 = 0x0 ec_atomic = 0x0 ecType = 0
__pSETLS = 0x000001EE92629720 __pSEParams = 0x000001EE92629E60
SEInternalTLS @0x000001EE92629720
---------------------------------
m_activeHeapDatasetList = 0x000001EE92629B30
m_activeIndexDatasetList = 0x000001EE92629B40 m_flags = 0
m_TLSstatus = 3 m_CriticalOpDbId = 65535 m_CloudHostDbId = 65535
m_RestoringDbId = 65535 m_RestoreTargetDbId = 0 m_noLockScanCount = 0
m_readonlyDatabaseScan = false m_inCatchupRedo = false
m_pBulkOpLockNotification = 0x0000000000000000 m_pDbccContext = 0x0000000000000000
m_pCompressionContext = 0x0000000000000000
m_pRetentionCleanupContext = 0x0000000000000000 m_pAllocFileLimit = 0x0000000000000000
m_dekInstanceIndex = 0x-1 m_pImbiContext = 0x0000000000000000
m_pNcciThreadContext = 0x0000000000000000
SEParams @0x000001EE92629E60
----------------------------
m_lockTimeout = -1 m_isoLevel = 4096 m_logDontReplicate = 0
m_neverReplicate = 0 m_XactWorkspace = 0x000001EEFA4EE040
m_execStats = 0x000001E4734EBB60
所有的Dump文件都指向一个存储过程,而最终发现是SQL Agent上的一个作业调用这个存储过程。而咨询微软Supprt的同事,人家反馈是因为这个存储过程使用了oracle linked server ,而且因为在OraOLEDB.Oracle驱动上勾选了“Allow InProcess”选项的缘故,具体邮件如下:
Hello xxxxx,
Many thanks for the feedback. If this is the case, there is a known issue when running queries through an Oracle linked server, which you can find in the following article:
This happens because it is not recommended to have external modules loaded into the SQL Server memory, as they can cause these types of unexpected behaviors. To try and troubleshoot this issue I propose the following action plan:
- In the SSMS, open “Server Objects” -> “Linked Servers” -> “Providers”
- Select the OracleDB provider, right click and go to “Properties”
- In the “Properties” window uncheck the “Allow InProcess” option
- Reboot the server
This process will remove from the SQL Server memory those DLLs and this should prevent the issue from happening again. Let me know if this plan would be possible to execute from your side and, if so, tell me how it went once it is done.
I will be waiting on your feedback, if you have any questions in the meantime feel free to reach out to me.
Best Regards,
虽然微软的技术支持反馈出现Dump文件是因为OraOLEDB.Oracle驱动上勾选了“Allow InProcess”选项的缘故,但是他提供的官方文档是SQL 2005、2008的相关文档,而不是SQL Server 2017d的相关文档,而且在SSMS里面调用Oracle Linked Server不报错。这个让我有点质疑其答复。后面按照其要求处理后,确实发现SQL Dump文件消失了。下面是对整个过程的一个复盘:
1: 当初在OraOLEDB.Oracle驱动上勾选了“Allow InProcess”选项,是因为开发使用OPENQUERY查询时,报错如下错误
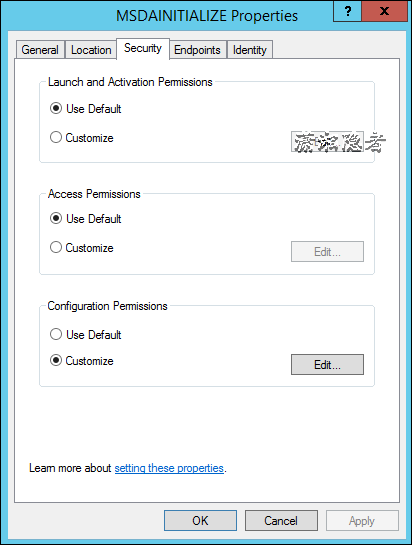
其实出现这个错误,是因为启动SQL Server实例的账号是NT Service\MSSQLSERVER, 如果是LocalSystem等这类账号就不会报这个错误。主要是因为MSDAINITIALIZE Properties的安全设置。
Click Start, type Dcomcnfg in the Search programs and files box, and then press Enter.
Expand Component Services, expand Computers, expand My Computer, and then click DCOM Config.
Right-click MSDAINITIALIZE, and then click Properties.
On the Security tab, under Launch and Activation Permissions, click Customize, and then click Edit.
Add the Administrators group or the user account that you want.
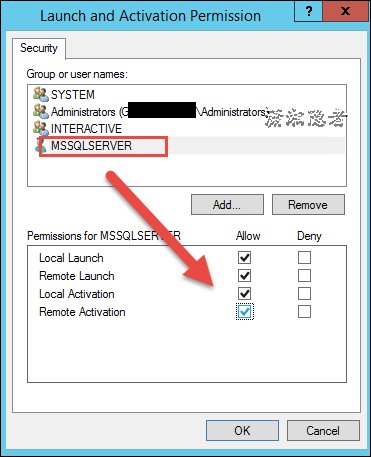
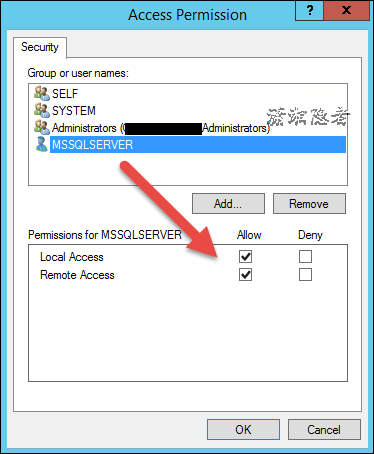
如下所示,在安全选项里面使用“Customize"里面,加上启动SQL Server服务(NT Service\MSSQLSERVER)或SQL Server Agent服务的账号(NT Service\SQLSERVERAGENT)的权限,如下所示:
详细步骤参考下面过程
Verify below settings in DCOMCNFG: Start --> Run –> Dcomcnfg
1. Component services -->My Computer ---> Properties verify that below options are set:
In the 'Default Properties' tab:
- 'Enable Distributed COM on this computer' is checked.
- Default Authentication = Connect.
- Default Impersonation Level = Identify or Impersonate.
2. Component services --> My computer --> DCOM Config --> MSDAINITIALIZE
-Right click on MSDAINITIALIZE --> Properties -->Security
-Add the SQL Server service account (if connected to SQL server using SQL login) or windows user account under "Launch and Activation Permissions", "Access permissions" and "Configuration Permissions".
-Give full rights to these accounts.
-Restart the server
回到之前问题,取消了OraOLEDB.Oracle驱动上的“Allow InProcess”选项后,SQL Dump文件缺失消失了。也就是说这个确实是因为“SQL Server service crashes when you run an Oracle linked server query” 这个缘故导致的。不过在测试过程中,我简单的查询是不会触发这个bug。尚不清楚内部的具体原因,另外,还有就是有些版本勾选了这个选项,也没有触发这个Bug。目前只在SQL Server 2017 (RTM-CU14) (KB4484710) - 14.0.3076.1 (X64) 这个版本中发现了这个问题。
参考资料: